

Michelle Drolet
Discover the looming threat of AI-powered social engineering and how it can and will target your employees. We will discuss AI Risk, AI User Awareness and Training, the Dark Side of AI, and how bad actors are leveraging AI in their attacks right now. Learn vital steps to safeguard your company against these emerging threats, and explore the deceptive potential of generative AI.


Michelle Drolet
Discover the looming threat of AI-powered social engineering and how it can and will target your employees. We will discuss AI Risk, AI User Awareness and Training, the Dark Side of AI, and how bad actors are leveraging AI in their attacks right now. Learn vital steps to safeguard your company against these emerging threats, and explore the deceptive potential of generative AI.

Michelle Drolet
Discover the looming threat of AI-powered social engineering and how it can and will target your employees. We will discuss AI Risk, AI User Awareness and Training, the Dark Side of AI, and how bad actors are leveraging AI in their attacks right now. Learn vital steps to safeguard your company against these emerging threats, and explore the deceptive potential of generative AI.


Michelle Drolet


Michelle Drolet


Michelle Drolet
What takes a big hit yet is typically on the bottom of the priority list? Web Applications. Join Michelle Drolet – CEO & Founder of Towerwall and Josh Davies – Principal Technical Product Marketing Manager of Fortra’s Alert Logic.


Michelle Drolet
We invite you and your colleagues to join Towerwall and Pentera for our next BrightTALK where we will be discussing how to build a solid vulnerability management program with people, process, and technology.
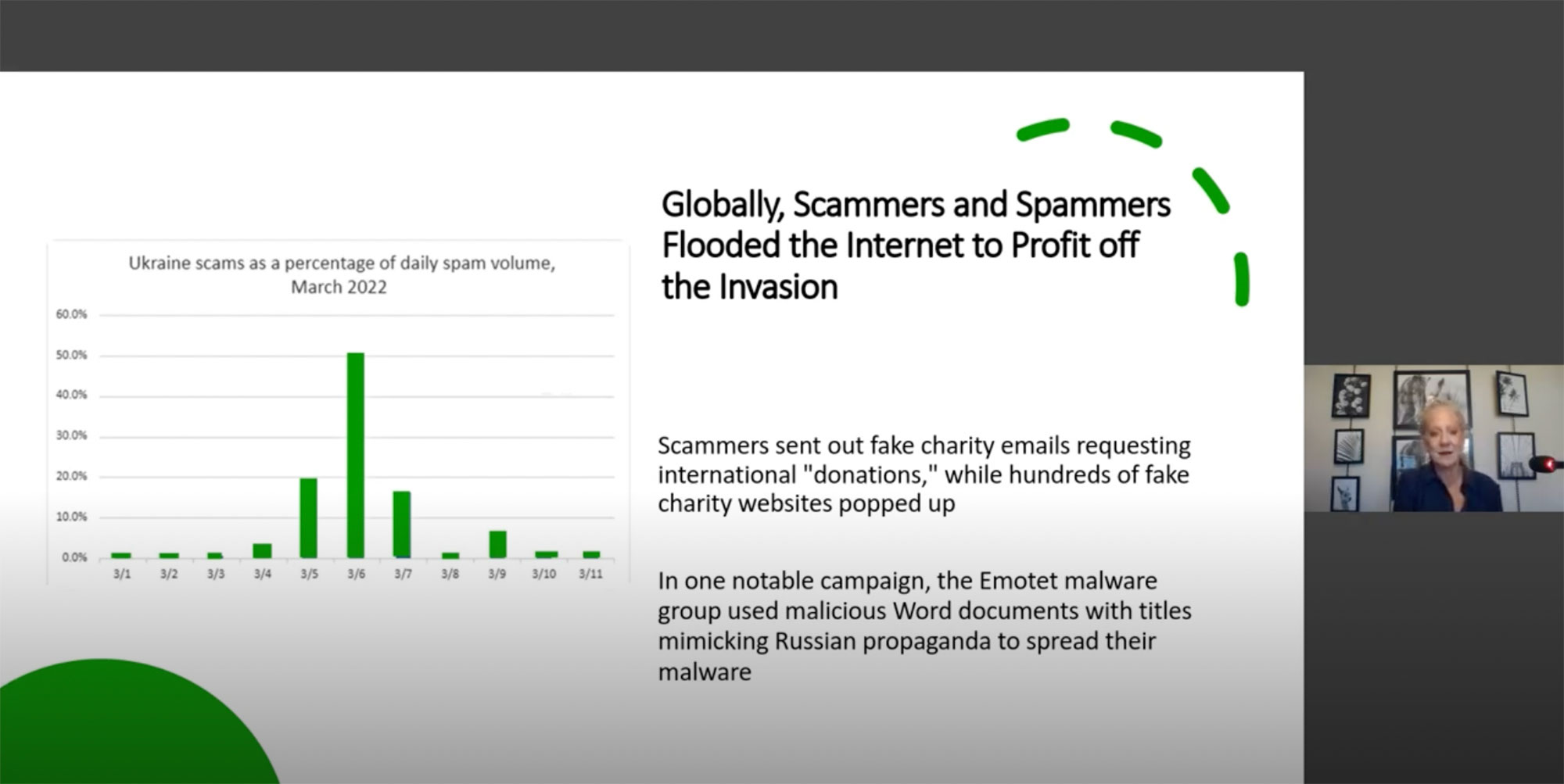
What does your cybersecurity posture look like in 2023? Tune into this webinar from Towerwall Founder and CEO Michelle Drolet as she discusses the latest cyberthreat trends and provides the necessary insights to defend against evolving attacks.

Michelle Drolet
While the ransomware game seems to be ever-changing, it is our job to be proactive in our preventative methods. The first step in managing ransomware attacks is ensuring that they don’t happen. We invite you and your colleagues to join Towerwall and Alert Logic for our next BrightTALK where we will be discussing how advanced threat intelligence is necessary in order to be proactive in detecting and responding to such attacks.


Michelle Drolet
Now more than ever, keeping you and your business secure is key. We invite you and your colleagues to join us for our cybersecurity webinar where we will be discussing how to secure and keep your Cyber Insurance in 2022.

Michelle Drolet
Please join cybersecurity experts Michell Drolet, Founder and CEO of Towerwall, and Sam Heard, President of Data Integrity Services to learn how you can understand and protect key elements across your diocese including parishes, institutions, schools, and charities.

Michelle Drolet
Data breaches are increasingly on the rise; cyber attacks continue to evolve in sophistication, businesses must remain vigilant and informed and arm themselves with the right tools and strategies to defend themselves when the inevitable happens.


Michelle Drolet
It is important to remember that, even if we think our environments are completely secure, there is always the potential for a breach. So how do we remain secure? Join Michelle Drolet and Bharath Vasudevan as they examine how the “Layers of Defense Method” is the key to security.


Michelle Drolet
Learn from our panel of experts as they discuss Privacy, Security and Compliance and how to effectively navigate the ever-evolving compliance mandates and regulations. – Learn how to make information security actionable.


Michelle Drolet
Hear from our resident expert as he discusses best practices for cloud-based forensics.


Michelle Drolet
Live online Friday, July 10th 12:00 – 1:00 p.m. EST Panelist include: Michelle Drolet, Towerwall & Jason Klein, Offit Kurman The threats are real and increasing daily. Learn how you can protect yourself and your cannabis company from unauthorized access to confidential files and proprietary data. By now, we are all too familiar with the


Michelle Drolet
Live online July 2, 2020 12:00 pm ET Panelist include: Michelle Drolet, Towerwall, Itay Nachum, Safe-T, Scott Tingley, Cogito & Tom Ward, Qnext Data breaches are on the rise, highlighting no organization is safe from cyberattacks. One cause is that workforce mobility and cloud computing has placed most workloads beyond the shelter of corporate networks

Michelle Drolet
Live online Thursday, May 28 at 3:30 p.m. ET Cyberthreats morph rapidly as they try to stay ahead of our defenses; wearing new disguises and breaking down virtual barriers in unique ways. The answer to, “How do I remain secure?” changes as quickly as the cyberthreats we face. Join us for an interactive Q&A Panel


Michelle Drolet
Join our partner Pcysys for their latest webinar: What’s New in PenTera Thursday, March 26th 3:00 PM GMT | 10:00 AM EST In the upcoming What’s New webinar, we’ll go over the new features and enhancements in PenTera version 4.0. You’ll learn about our new: Revamped User Interface Direct Access to Entire Remediation Wiki Web


Michelle Drolet
Cloud security is simpler than you think. Move to the cloud with confidence while increasing the efficiency of your security management, compliance, and governance. Listen in to learn how you can: Secure once and run everywhere: manage a multi-layered security strategy across your data center and cloud from a single console. Secure every cloud and


Michelle Drolet
It may seem like a peculiar twist of irony, but as the technical capabilities afforded by automation proliferate, successful cyberattacks are increasingly more reliant on human execution. Join this 60-minute presentation to learn more about the cyber threat landscape, threat hunting and response techniques, and real-world examples of how Sophos Managed Threat Response detects and


Michelle Drolet
Expert panelists Michelle Drolet of Towerwall and Tom Ward of Qnext/FileFlex joined participants online on October 1st 2019 to speak about how to use a decentralized edge-cloud architecture to secure your company’s files & data and prevent cybersecurity threats and ransomware attacks. Watch the full webinar below:


Michelle Drolet
How to secure remote file access, sharing and collaboration with decentralized cloud computing. When: Tuesday, October 1, 2019 – 2:00 PM EST Sponsored by: Sponsored by Towerwall and Qnext Presented by: Michelle Drolet, Paul Barker Register now >


Michelle Drolet
Workloads in the public cloud are the new pot of gold for savvy cybercriminals. Often misconfigured and under-secured, they’re an easy way for hackers to steal data and take advantage of your processing power. If you use Amazon Web Services, Microsoft Azure, or Google Cloud Platform, or are thinking about migrating to any of these,


Michelle Drolet
As cyber attacks become increasingly common, it is vital for organizations to be armed with the most effective tools and knowledge to prevent, detect and respond to cyber threats. Join this interactive Q&A panel with top security experts across the ecosystem to learn more about: Trends in Advanced Threat Detection & Vulnerability Management How to


Michelle Drolet
What is cyber threat intelligence, and how can organizations leverage it to identify threats and potential malicious activity in advance? Discover the best ways organizations can arm themselves with actionable threat intelligence to block cyber attacks or mitigate their impact. Join this panel of experts to learn more about: Cyber threat intelligence: What it is


Michelle Drolet
Cybersecurity, much like safety, cannot be achieved – it is an ongoing process that changes and adjusts to respond to the threat landscape, business needs and resources. As essential a cybersecurity strategy is to the enterprise, so is the implementation of it. Host: Michelle Drolet, CEO, Towerwall and Amy McLaughlin, Director of Information Services, Oregon

Michelle Drolet
What Exactly Is Automated Penetration Testing? Software-based penetration testing is here! Learn how leading companies are taking advantage of this new technology to drive cost-effective remediation. When: Wednesday, February 27th 2:00 PM EST Host: Amitai Ratzon CEO , Pcysys Your Takeaways: A fresh approach to vulnerability remediation prioritization How to ensure your security posture is kept


Michelle Drolet
Best Practices for Protecting Your Business from Cybercrime Cybercrime has evolved from random activities being carried out by individuals into a billion dollar illegal industry that continues to grow. How is cybersecurity keeping up with the rise of cybercrime? Join this panel of security experts to learn more about: Trends in cybercrime and lessons learned

Michelle Drolet
An Introduction to New Technology – Automated Penetration Testing In this webinar, we will review Automated Penetration Testing – principles, benefits, use cases, case studies, and live demo. When: Wednesday, January 16, 2019 2:00 PM ET Your Takeaways Understand the threat actors’ perspective of your company Learn of a different approach to vulnerability remediation prioritization

Michelle Drolet
Best Practices for Securing Your Organization in 2019 Data breaches are on the rise and getting their fair share of media attention. It is no longer a question of “if”, but “when” an organization will get breached. So, how are organizations preparing for the inevitable? When: Tuesday, January 15, 2019 11:00 AM ET About the

Michelle Drolet
The Rise of Targeted Ransomware What is targeted ransomware? Are you susceptible? What can you do to defend against it? Presented by: Michelle Drolet, CEO, Towerwall Watch now >

Michelle Drolet
Trends in Data Breaches and Comprehensive Responses Does your organization have a data breach response plan? Join Michelle Drolet and a team of industry experts for an interactive Q&A panel and discover the best practices for breach response and how to strengthen your organization’s cyber resilience. About the Webinar Join this interactive Q&A panel with


Michelle Drolet
Trends in Data Breaches and Comprehensive Responses Does your organization have a data breach response plan? Join Michelle Drolet and a team of industry experts for an interactive Q&A panel and discover the best practices for breach response and how to strengthen your organization’s cyber resilience. When: Wednesday, September 19, 2018 8:00 AM ET About


Michelle Drolet
Click here to watch the webinar now > Our own Michelle Drolet will be discusses the need for developing a solid Incident Response Program and doing Tabletop exercise throughout the year. An Incident Response Plan (IRP) will ensure information security incidents, once identified, will be handled and communicated appropriately. Consistency of how incidents are handled


Michelle Drolet
How to Build a Robust Incident Response Capability for Financial Institutions Our own Michelle Drolet will be discussing the need for developing a solid Incident Response Program and doing Tabletop exercise throughout the year. An Incident Response Plan (IRP) will ensure information security incidents, once identified, will be handled and communicated appropriately. Consistency of how


Michelle Drolet
Click Here to Watch the Webinar Now > View the Presentation > About the Webinar Enterprises face an exploding number of unmanaged and IoT devices on their networks, and cyber attacks are increasingly targeting these vulnerable devices. Join Armis and Towerwall to learn about 8 ways that you can secure your enterprise from these

Michelle Drolet
Click Here to Watch the Webinar Now > About the Webinar The deadline for the new European General Data Protection Regulation (GDPR) is four months away, and it is likely to affect most companies around the world in one way or another – even ones not based in Europe. Join our friends from Sophos


Michelle Drolet
Countdown to GDPR: Get the Competitive Edge Webinar featuring Sophos, Twinstate and Towerwall When: Wednesday, January 24, 2018 12:00 – 1:00 PM EST About the Webinar The deadline for the new European General Data Protection Regulation (GDPR) is four months away, and it is likely to affect most companies around the world in one way


Michelle Drolet
Click here to watch our latest webinar from our “Lunch with a vCISO” series >


Michelle Drolet
Join us for our second live webinar: Second Nature Security: More Secure Networks through Behavior Modification, Security Awareness and Training Wednesday, December 13, 2017 | 12:00 PM EDT – 1:00 PM EDT Join us for a vCISO roundtable discussion featuring: Michelle Drolet, Founder & CEO of Towerwall Greg Neville, vCISO & Sr. Security


Michelle Drolet
Happy National Cyber Security Awareness Month! Kick off October with our recent Lunch with a vCISO webinar “Do You Know Your Risk Tolerance – The Role of a vCISO.” Listen Now >


Michelle Drolet
Each session will provide unprecedented access to the industry’s top Virtual Chief Information Security Officers and cover critical issues in the field. The interactive series will cover a variety of topics, such as aligning information security policies with your firm’s culture and how to prepare for an audit. Attendees will be given the opportunity to


Michelle Drolet
Last week we hosted an informative webinar on today’s ransomware threats with our security partner Sophos. Watch a recording of the webinar below. I am sure you are seeing the explosion of ransomware in the headlines. Businesses of every size are targets and analysts estimate ransomware is on pace to be a $1B/year crime in


Michelle Drolet
Check out one of the upcoming complimentary partner webinars: Brute Force Attacks: Keeping the Bots at Bay with AlienVault USM Tuesday, October 11th 10:00am CST / 4:00 PM BST Hosted by AlienVault Brute force attacks are relatively simple for attackers to implement and they can wreak havoc on your organization if you don’t detect


Michelle Drolet
Towerwall & SnoopWall Complimentary Webinar: Breach Prevention & Near-Term ROI Tuesday, July 26 11:00am – 12:00pm EST Register Now > Today’s hyper-aggressive cyber landscape finds 40% of organizations are breached and the threat of regulatory and compliance fines are impacting productivity and business operations. 95% of these breaches occur behind firewalls on antivirus protected endpoints.