
Michelle Drolet
Discover the looming threat of AI-powered social engineering and how it can and will target your employees. We will discuss AI Risk, AI User Awareness and Training, the Dark Side of AI, and how bad actors are leveraging AI in their attacks right now. Learn vital steps to safeguard your company against these emerging threats, and explore the deceptive potential of generative AI.


Michelle Drolet
Religious organizations, Houses of Worship (HoWs) and missionaries (schools, hospitals, non-profits) often carry a false notion that they are at least risk of cyber-attacks (compared to ordinary businesses), because they are not involved in buying and selling of commercial goods and services. Contrary to this popular belief, cybercriminals have been regularly targeting churches, catholic organizations, and even the Vatican.


Michelle Drolet
In an era where data breaches and cyber threats loom, the security of patient information in plastic surgery practices (PSPs) is more critical than ever. Envision a scenario where, in a mere moment, the confidential data of your patients is at risk, posing a serious threat to the trust they place in your practice and
6 Minute 21 Second Read


Michelle Drolet
In 2024, for cybersecurity, we’re entering an era where advanced AI tools and intricate social engineering tactics (especially during election years) are changing the game. To avoid potential cyber threats, businesses, governments and individuals must grasp these emerging trends. Trend 1. Rise Of Cybersecurity AI In 2024, AI’s role in cybersecurity will expand to encompass automated
4 Minute 29 Second Read


Michelle Drolet
Cyber threats such as ransomware, phishing and data theft pose significant risks to cannabis dispensaries. These attacks can disrupt operations with long recovery delays, compromise client data, invite litigation and damage business reputations. IBM says the average global cost of a data breach is $4.45 million, prompting 51% of organizations to raise their security budgets. Implementing security measures
4 Minute 31 Second Read


Michelle Drolet
The cybersecurity skills gap situation has become a vicious cycle. On one hand, 63% of cybersecurity professionals complain that working conditions have become more difficult over the last two years owing to a heavy surge in cyberattacks, mounting data privacy concerns, overwhelming workloads, budget restrictions, staffing shortages and a complex regulatory environment. On the other hand, 71% of
4 Minute 59 Second Read

A need for organizations to strengthen their third-party risk management practices. The Securities and Exchange Commission (SEC) recently charged software company SolarWinds and its Chief Information Security Officer (CISO) with fraud and internal control failuresOpens a new window. The prospect of a public CISO being indicted will be chilling to other C-suite members, calling into question
4 Minute 34 Second Read


Janelle Drolet
10. Isolate infected systems. Just as we had to quarantine for Covid infections, power down compromised endpoints to avoid spreading the contagion to other parts of the network. 9. System recovery. Create, review, and exercise a system recovery plan to ensure the restoration of services as part of a comprehensive disaster recovery strategy. This may
1 Minute 48 Second Read

In this Insight article, Michelle Drolet, Founder of Towerwall, discusses the key enhancement and practical insights offered by the newly released NIST Cybersecurity Framework 2.0 (CSF 2.0). The US National Institute of Standards and Technology (NIST) just released a new update to its Cybersecurity Framework, the NIST CSF 2.0. This new version is currently in
4 Minute 39 Second Read


Michelle Drolet
Consider this advice to successfully replace a perimeter approach to security with a zero trust framework. Despite organizations upping their spend on cybersecurity technology, infrastructure, and services each year, threat actors are still finding ways to slip through the cracks. There are two main reasons for this: One, human error: Unfortunately, many users still don’t take security
5 Minute 2 Second Read


Michelle Drolet
If you’re an existing Amazon Web Services customer or are considering migrating to AWS, it’s likely you have major concerns around security. Cloud security has become a top risk and a top priority for enterprises because cloud assets are becoming the biggest targets for cyberattacks. No doubt, AWS does everything it possibly can to protect itself and its customers; however, the
4 Minute 10 Second Read

Michelle Drolet
When mechanized looms were first introduced, workers protested because they feared the automation would rob them of their skilled craft. When ATMs first arrived, some foretold the demise of bank tellers. When self-service kiosks were introduced, everyone believed they would replace cashiers. While technological shifts may have caused job losses in certain sectors, it could
4 Minute 3 Second Read


Michelle Drolet


Michelle Drolet
Last week, Microsoft patched two zero-day vulnerabilities (CVE-2023-36884 and CVE-2023-38180). These vulnerabilities are part of Microsoft’s August 2023 Patch Tuesday, which also includes security updates for 87 vulnerabilities. Both of these vulnerabilities were exploited in cyberattacks, and one of them was publicly disclosed prior to the patch release. CVE-2023-36884 CVE-2023-36884 is a remote code
2 Minute 18 Second Read


Michelle Drolet
Disasters and cybersecurity incidents are inevitable. The unprepared are hit the worst, and the consequences can range from massive monetary and reputational damages to outright business closure. A recent study suggests enterprises can lose up to $5 million per hour in unexpected operational disruptions and data loss events. The only way around this is to stay alert
4 Minute 55 Second Read


Michelle Drolet

Michelle Drolet
Large language models (LLMs) like ChatGPT and Google Bard have taken the world by storm. While these generative AI programs are incredibly versatile and can be implemented in a wide range of productive business use cases for the good, there is also a potential downside for LLMs to empower threat actors, adversaries and cybercriminals with
4 Minute 30 Second Read


Michelle Drolet
10. Benefits & risks. Like most tools, large language models (like ChatGPT & Google Bard) can be used for good or ill purposes. Positives: generate creative content, translate languages, and debug software. Negatives: They can be used to damage reputations, spread misinformation, code malware, and conduct cyberattacks. 9. Phishing at scale. LLMs can be used
1 Minute 36 Second Read


Michelle Drolet
What takes a big hit yet is typically on the bottom of the priority list? Web Applications. Join Michelle Drolet – CEO & Founder of Towerwall and Josh Davies – Principal Technical Product Marketing Manager of Fortra’s Alert Logic.


Michelle Drolet
Audits can help companies identify weaknesses and make a company more resilient in the event of a cyberattack. Washington, D.C. magazine CFO reports financial auditors are increasingly concerned about cybersecurity, demanding greater transparency on how organizations are managing and mitigating cyber risk. And why shouldn’t they? A cyberattack or a data breach can lead to major financial
4 Minute 12 Second Read


Michelle Drolet
A major vulnerability in DNA sequencing equipment was discovered, highlighting the risks of cyberattacks on medical devices. The vulnerability was found, of all things, in DNA sequencing equipment made by San Diego biotech firm Illumina; discovered by its security team and subsequently patched. Such an intrusion could expose sensitive patient data or allow threat actors
2 Minute 25 Second Read


Michelle Drolet
Almost every other week, we hear or read stories about some high-profile organization experiencing a data leak. In the U.S. alone, there were about 1,802 publicly reported incidents last year that resulted in 4.2 billion private records being leaked online. This is only a tip of the iceberg since plenty of organizations that suffer leaks won’t usually
4 Minute 30 Second Read


Michelle Drolet
The threat landscape continues to change as bad actors refine their cybercrime tactics and expand their attack options. Cyberattacks continue to break new records and bad actors keep getting better at what they do. The only way organizations can truly defend themselves is by gaining an understanding of how cyber threats are evolving, acquiring the knowledge
0 Minute 30 Second Read


Michelle Drolet
What You Need to Know: A zero-day vulnerability (CVE-2023-28252) was found in the Windows Common Log File System (CLFS) and is being actively exploited. The vulnerability allows attackers to gain SYSTEM privileges on target Windows systems and deploy Nokoyawa ransomware payloads. CISA’s Known Exploited Vulnerabilities catalog now includes CVE-2023-28252, which impacts all versions of supported
1 Minute 15 Second Read


Michelle Drolet
We invite you and your colleagues to join Towerwall and Pentera for our next BrightTALK where we will be discussing how to build a solid vulnerability management program with people, process, and technology.


Michelle Drolet
The rising number and increasing severity of ransomware attacks are sufficient to prove that current cybersecurity strategies are simply not working. The fact is, today’s security approaches are far too focused on the network perimeter and too lenient when it comes to internal traffic. And since most users, devices and cloud-based applications operate outside of the corporate
4 Minute 56 Second Read
What does your cybersecurity posture look like in 2023? Tune into this webinar from Towerwall Founder and CEO Michelle Drolet as she discusses the latest cyberthreat trends and provides the necessary insights to defend against evolving attacks.


Michelle Drolet
Recent bank failures are creating opportunities for cybercriminals to readily access your personal and company bank accounts. With the vast uncertainty, cybercriminals are posing as representatives from banks, requesting account information and gaining immediate access to remove your money and change your login information. We encourage you to be vigilant and verify all communication you may
1 Minute 17 Second Read


Michelle Drolet
Editor’s Note: All the text in bold below was written by the ChatGPT artificial intelligence. Those sections were verified as accurate by a human editor, but they have not been changed. 10) ChatGPT is a language model developed by OpenAI, a research organization dedicated to creating and promoting friendly artificial intelligence (AI). Free for now,
1 Minute 45 Second Read


Michelle Drolet
What You Need to Know: In response to attacks aimed at hacking iPhones, iPads, and Macs, Apple issued urgent security updates that address two vulnerabilities, one of which is a zero-day vulnerability. The first vulnerability, tracked as CVE-2023-23529 [1,2], is a WebKit confusion zero-day that can lead to OS crashes and the execution of arbitrary
1 Minute 47 Second Read


Janelle Drolet
Janelle Drolet was recently named The Most Admired Women Leaders in Business, 2023 by CIO Views It’s a sad fact of doing business – criminal hackers are continuously evolving their tactics to breach defenses, steal intellectual property and deploy ransomware. To combat them, a business needs leadership capable of keeping the company’s security controls
4 Minute 33 Second Read


Michelle Drolet
Michelle Drolet was recently named The Most Admired Women Leaders in Business, 2023 by CIO Views Many people equate money with success. Although, money is not a bad indicator, but it is not the end all be all. To me success is being blessed with a beautiful family, my Towerwall team members and our
7 Minute 10 Second Read


Michelle Drolet
The Commonwealth of Massachusetts may soon approve a data privacy bill called the Massachusetts Information Privacy and Security Act, which will make the state a national leader in regulation of data privacy and security. There are extensive fines and penalties for non-compliance, and the ruling will allow individuals to sue organizations for data breaches. Who
2 Minute 15 Second Read


Michelle Drolet
What You Need to Know: A vulnerability was found in the open source JsonWebToken (JWT) library. According to Palo Alto Networks Unit 42, CVE-2022-23529 it could allow an attacker to achieve remote code execution (RCE) on a server verifying a maliciously crafted JSON web token request. The vulnerability impacts JsonWebToken package version 8.5.1 and earlier.
1 Minute 59 Second Read


Michelle Drolet
It’s that time of year again when we try to predict what’s ahead of us in terms of cybersecurity. 2022 has already become a record-breaker for the sheer volume of phishing scams, cyberattacks, data breaches and crypto heists. There was also a rise in hacktivism cases where state-sponsored cyber legions disrupted critical infrastructure and services,
4 Minute 28 Second Read


Michelle Drolet
Ransomware attacks and ransomware attackers are both evolving, becoming much more complex and damaging with each passing year. Attackers are moving in and out of victims swiftly, encrypting systems or exfiltrating data well before security teams can detect their presence. What organizations need is an offensive approach in which cyber threats and adversaries are hunted down
4 Minute 15 Second Read


Michelle Drolet
What You Need to Know: There are two zero-day vulnerabilities affecting Microsoft Exchange Server 2013, 2016, and 2019. CVE-2022-41040 is a Server-Side Request Forgery (SSRF) vulnerability and CVE-2022-41082 is a vulnerability that allows for remote code execution when PowerShell is accessible to a threat actor. Microsoft stated that the current attacks are limited but the
3 Minute 1 Second Read

Michelle Drolet
While the ransomware game seems to be ever-changing, it is our job to be proactive in our preventative methods. The first step in managing ransomware attacks is ensuring that they don’t happen. We invite you and your colleagues to join Towerwall and Alert Logic for our next BrightTALK where we will be discussing how advanced threat intelligence is necessary in order to be proactive in detecting and responding to such attacks.


Michelle Drolet
SMBs face the same threats as larger companies but are challenged with limited resources, budgets and security talent. Organizations that outsource with an experienced security partner can make up for shortfalls in expertise and resources. In 2021, 40% of SMBs experienced a security breach partly because they are low-hanging fruit and attractive targets for leapfrogging to a
4 Minute 39 Second Read


Michelle Drolet
Now more than ever, keeping you and your business secure is key. We invite you and your colleagues to join us for our cybersecurity webinar where we will be discussing how to secure and keep your Cyber Insurance in 2022.


Michelle Drolet
What You Need to Know: Apple released security updates for vulnerabilities found in iOS, iPadOS, MacOS Big Sur, and macOS Monterey. CVE-2022-32894 and CVE-2022-32893 are zero-day flaws that have code execution vulnerabilities being exploited by attackers in the wild. There are few details surrounding the vulnerabilities or how they were used, but the flaws are
1 Minute 37 Second Read


Michelle Drolet
What You Need to Know: A large-scale phishing campaign was disclosed by ThreatLabz this week. The researchers observed the use of advanced phishing kits in a large campaign primarily targeting corporate enterprise users of Microsoft email servers. The threat actors behind the campaign have not been identified, but researchers observed the attackers using an adversary-in-the
2 Minute 30 Second Read


Michelle Drolet
What You Need to Know: A hardcoded credentials vulnerability was found in the Questions for Confluence app and is under active exploitation. The vulnerability allows remote, unauthenticated attackers that know the hardcoded password for specific accounts in the app, to gain access to non-restricted pages in Confluence. CVE-2022-26138 was observed to be under active exploitation
1 Minute 52 Second Read


Michelle Drolet
We were honored to have our Director of Sales, Janelle Drolet, present at the AWS re:Inforce yesterday in Boston. We were excited to share the unique partnership of Towerwall, Alert Logic, and AWS. Learn more about the Towerwall and Alert Logic MDR difference.
0 Minute 13 Second Read


Michelle Drolet
First of all, thank you! With your help, Towerwall, along with our partners SentinelOne, Proofpoint and Alert Logic are proud to announce the donation of $1,600 to MassBay’s Cybersecurity Scholarship Fund. The funds were raised as part of Towerwall’s recent Annual Security Summit. The Bi-annual Sessions and Annual Summit create an open forum for knowledge
1 Minute 34 Second Read


Michelle Drolet
What You Need to Know: A zero-day vulnerability was found in the latest Widows 11 and Windows Server 2022 releases. CVE-2022-22047 is a local privilege escalation vulnerability found in the Windows Client and Windows Server Runtime Subsystem. Although Microsoft has issued a patch, the vulnerability is actively being exploited by attackers and has a CVSS
2 Minute 57 Second Read


Michelle Drolet
What You Need to Know: Over the Fourth of July weekend, Google released a patch for a high-severity zero-day Chrome vulnerability. The vulnerability is being exploited in the wild and affects Google Chrome and other chromium-based browsers. The heap-based buffer overflow vulnerability is found in the WebRTC (Web-Real-Time Communications) component. The vulnerability is being tracked
2 Minute 1 Second Read


Michelle Drolet
Thank you to all that joined us at our Cybersecurity Executive Session this past Thursday. It was an amazing event with great discussion from industry leaders. A huge thank you to our presenting partners: MassBay Community College, Alert Logic, Sentinel One and Proofpoint. As in years past, all proceeds of the event will go to
1 Minute 46 Second Read


Michelle Drolet
What You Need to Know: A ransomware attack was deployed against an unnamed target, using Mitel’s VoIP appliance an entry point. CVE-2022-29499 is actively being used by attackers to achieve remote code execution and to gain initial access to their victim’s environment. The vulnerability is rated 9.8 in severity on the CVSS vulnerability scoring system.
2 Minute 48 Second Read


Michelle Drolet
What You Need to Know: Today, VMware issued patches for two security flaws discovered in Workspace ONE Access, Identity Manager, and vRealize Automation. The vulnerabilities are tracked as CVE-2022-22972 and CVE-2022-22973 and could be exploited to backdoor enterprise networks. The first vulnerability, CVE-2022-22972 has a critical CVSS score of 9.8 and is an authentication bypass
3 Minute 39 Second Read


Michelle Drolet
Think about this for a moment — global CEOs rank cyber risk as a top concern ahead of macroeconomic volatility, health risks, climate change or even geopolitical crises. What’s worse, they represent organizations that are deploying top-tier security tools, teams and security measures. So where is everyone going wrong? Truth is, cybersecurity is more than just committing
4 Minute 6 Second Read


Michelle Drolet
Organizations collect, store and process vast amounts of data today. Employee information, supplier information, customer information, intellectual property, financial records, communication records—all common types of data that ordinarily exist in almost every business. When organizations fail to secure or protect this data, it exposes them to a host of business risks like breaches, financial losses,
4 Minute 51 Second Read


Michelle Drolet
BOSTON, March 10, 2022 (Newswire.com) – Towerwall, a cybersecurity preparedness and consulting services firm, today announced that its Founder and CEO Michelle Drolet was named to the inaugural SIA Women in Security Forum Power 100 honoree list sponsored by the Security Industry Association (SIA), a trade association for global security solution providers with over 1,200 member companies that help
2 Minute 25 Second Read


Michelle Drolet
What You Need to Know: This week, ESET researchers discovered three new cyberattacks against Ukraine: HermeticWizard, HermeticRansom, and IsaacWiper. There is a new exploit, HermeticWizard, which spreads HermeticWiper across local networks via WMI and SMB. HermeticWizard is a worm that was deployed on a Ukrainian system on February 23, 2022. The malware starts by trying
6 Minute 13 Second Read


Michelle Drolet
Religious organizations, Houses of Worship (HoWs) and missionaries (schools, hospitals, non-profits) often carry a false notion that they are at least risk of cyber-attacks (compared to ordinary businesses), because they are not involved in buying and selling of commercial goods and services. Contrary to this popular belief, cybercriminals have been regularly targeting churches, catholic organizations, and even the Vatican.

Michelle Drolet
Businesses are gearing up for another bumpy year of cybercrime. An ongoing barrage of phishing and ransomware attacks, third-party breaches like those involving Log4j and SolarWinds and the surge in remote work are but a few of the many reasons why almost 80% of security leaders still lack confidence in their cybersecurity posture. In response, a majority of them are planning to significantly
3 Minute 59 Second Read

Michelle Drolet
Please join cybersecurity experts Michell Drolet, Founder and CEO of Towerwall, and Sam Heard, President of Data Integrity Services to learn how you can understand and protect key elements across your diocese including parishes, institutions, schools, and charities.

Michelle Drolet
Data breaches are increasingly on the rise; cyber attacks continue to evolve in sophistication, businesses must remain vigilant and informed and arm themselves with the right tools and strategies to defend themselves when the inevitable happens.

Michelle Drolet
FTC warns businesses that failure to address critical vulnerability could result in legal action. On Dec. 9, the Apache Software Foundation issued a Log4j security alert that a vulnerability (CVE-2021-44228), aka Log4Shell, allows unauthenticated users to remotely execute or update software code on multiple applications via web requests. On a scale of severity, the NIST has graded
4 Minute 6 Second Read


Michelle Drolet
This eBook strives to make the 20 security controls as described in detail by the SANS institute more accessible to everyday business people.
Taking any one of these 20 actions on the list will have a positive impact on your security status, but the smart move is to work towards fulfilling all 20 of these recommendations. These are simple common-sense rules, but you’d be amazed at how often they’re overlooked.


Michelle Drolet
This holiday season, we are proud to announce we have made a donation to a new scholarship fund aimed at supporting young women and minority students to pursue rewarding careers in cybersecurity. Long-time colleague and client, United States Air Force Veteran, Saeed Garner, Director of Information Security for Christian Care Ministry, founded the newly established
1 Minute 47 Second Read


Michelle Drolet
What You Need to Know: Security teams are in a hurry to patch an unknown active vulnerability that was found in Apache’s Log4j and is now named Log4Shell. Log4j is a Java-based open-source library used by apps and services, and the newly found vulnerability could allow an attacker to compromise millions of devices across the
3 Minute 48 Second Read


Michelle Drolet
Traditional cybersecurity practices relied on the age-old maxim, an ounce of prevention is better than a pound of cure. But here’s the biggest truth about modern cybersecurity: There’s no such thing as foolproof security, and bug-free software is an oxymoron. From the ’90’s script kiddies to present-day state-sponsored actors and cybercrime syndicates, attacks have grown
4 Minute 18 Second Read


Michelle Drolet
If you have third-party partners, you need a third-party cyber risk management program. Here are six key steps to follow. Many organizations transact with hundreds of third-party partners, according to EY’s Global Third-Party Risk Management Survey 2019-2020, a trend that PwC finds shows no sign of slowing, even as the risks increase. A recent survey by security vendor Anchore found that in
3 Minute 47 Second Read

Michelle Drolet
BOSTON – August 31, 2021 – Towerwall, a 25-year provider of cybersecurity services for emerging to mid-size enterprises, today announced it has teamed up with Amazon Web Services (AWS) to list its array of data and IT security services and onsite deployment of Virtual Security Officers on the AWS Marketplace. Towerwall is one of the
2 Minute 28 Second Read


Michelle Drolet
According to Ponemon, 67% of respondents to a CISO survey believe hackers and cybercriminals are more likely to target their companies. In this regard, the role CISOs play in modern organizations has grown more critical, as they’re tasked with managing enterprise risk, securing Internet of Things (IoT) devices and deploying security analytics. To maximize the security of
4 Minute 7 Second Read

Michelle Drolet
It’s probably no surprise that the ideal method to validate security defenses, strengthen cybersecurity posture and prepare for a cyber incident is through simulation of a cyber-attack. Sports leagues, coaches and analysts have used the same technique to improve performance and boost defense capabilities of their teams.


Michelle Drolet
The landscape of cybersecurity insurance is shifting in the wake of a wave of high-profile ransomware attacks. Over the last five years, the U.S. has suffered more than 4,000 ransomware attacks a day, according to a U.S. government interagency report. It’s a pandemic unto itself: Ransomware attacks happen once every eight minutes. This trend has driven greater
4 Minute 54 Second Read


Michelle Drolet
Most people aren’t aware of what to look for when buying a cyber insurance policy. Since it is still a novel concept, you first need to determine your cyber risk, your risk tolerance and the costs of things that don’t have a clear monetary value (e.g., injury to your business’s reputation). What’s more, some insurance companies are still not fully certain as to how to underwrite cyber-insurance policies.


Michelle Drolet
For small to mid-size businesses (SMBs), knowing what you need to remain secure and setting a resilient plan in place is half the battle. With the average cost of a security breach nearing $4 million, organizations need to detect threats early. Threat monitoring, detection and response (MDR) services offer businesses a turnkey security response. Combined
4 Minute 54 Second Read


Michelle Drolet
For Georgia, Virgina, the Carolinas and other states, it was Jimmy Carter revisited as long lines and price spikes awaited motorists at the gas pumps. Some stations as far south as St. Petersburg, Fla. ran out entirely, worrying travelers making plans for Memorial Day weekend. We learned a few things from the Colonial Pipeline ransomware
2 Minute 20 Second Read


Michelle Drolet
Over 37 billion records were exposed in breach events in 2020 – by far the most records exposed in a single year, according to a recent report by Risk Based Security. How has remote working impacted your organization’s security posture? What lessons can security professionals learn from the recent wave of breaches and what steps
0 Minute 30 Second Read


Michelle Drolet
It is important to remember that, even if we think our environments are completely secure, there is always the potential for a breach. So how do we remain secure? Join Michelle Drolet and Bharath Vasudevan as they examine how the “Layers of Defense Method” is the key to security.


Michelle Drolet
We are proud to share that our founder and CEO, Michelle Drolet has been named as a “Top 25 Women in Cybersecurity” by The Software Report. See below for more information and to read more: “The women that comprise this year’s list have not only stepped up to new challenges in addressing cyber risks and
0 Minute 41 Second Read


Michelle Drolet
Navigating the vendor landscape is a challenge for many IT departments, particularly when looking at detection and response solutions, and especially since the cybersecurity industry is overly reliant on acronyms. EDR, MDR and XDR are three emerging endpoint security technologies built to provide greater visibility, threat detection and response across all corporate endpoints. With today’s
3 Minute 51 Second Read


Michelle Drolet
Modern cyber threats are growing in scope, cost and complexity. Hackers are continuously evolving their tactics to execute breaches, hold businesses at ransom and steal intellectual property. Globally, cybercrime is estimated to cost $10.5 trillion annually by 2025. To put things in perspective, the combined revenue of the world’s largest tech companies, Apple, Amazon, Alphabet and Facebook,
4 Minute 48 Second Read


Michelle Drolet
Selecting a Large-Scale, Secure and HIPAA-Compliant Covid Scheduling Solution A year ago, the coronavirus threw the world into a historic crisis. One industry pushed to the brink was the U.S. healthcare system. Now, with the arrival of life-saving vaccines, hospitals that were once tasked with treating waves of sick patients are now shifting gears to
1 Minute 56 Second Read

While Service Organization Control (SOC) 2 compliance isn’t mandatory, it can bring a range of benefits for your organization. Created by the AICPA (American Institute of Certified Public Accountants), this auditing process helps you to assess your data privacy and security standards. Once achieved, you will have a comprehensive set of security policies that will
8 Minute 1 Second Read


Michelle Drolet
Healthcare organizations have faced continual stress from heavy COVID-19 caseloads in 2020. Cyberattacks on their information networks also loomed as a serious threat, and the pressure to protect data is expected to grow this year, as more criminals target healthcare providers. Protecting patient data from unauthorized access has long been a regulatory prerequisite for healthcare
4 Minute 45 Second Read


Michelle Drolet
The pandemic has dominated the news in 2020, overshadowing everything else. We’ve seen a rapid rise in remote working, a wave of pandemic-related scams and pressure to modernize IT while cutting costs. As the dust settles on a tumultuous year, it’s time to plan ahead. IT departments were forced to accelerate their plans and roll
4 Minute 33 Second Read


Michelle Drolet
I wanted to reach out to provide you with important information on the recent hack that has impacted nearly 20,000 of SolarWinds customers. The attack, which dates back to October 2019, has impacted many sectors including government, hospitals, educational and technology organizations. Over 80% of the Fortune 500 companies have uncovered a breach in their
0 Minute 57 Second Read


Michelle Drolet
A dark web scan review from Alert Logic can help scan your company domain and discover when and whose credentials have been exposed and when exposure is discovered, you can then require affected employees to change their passwords.


Michelle Drolet
10) With so many people working from home on all sorts of devices, make sure these endpoints continue to receive the latest security patches and software operating system updates to lessen your chance of compromise. 9) Avoid running sensitive transactions (like banking) over public WiFi networks that are typically unsecured from eavesdropping. Using your smartphone
1 Minute 48 Second Read


Michelle Drolet
Penetration testing is vital, but are you doing it right? Here are some common mistakes and advice on how to avoid them. One of the most effective ways to uncover flaws and weaknesses in your security posture is to have a third party carry out planned attacks on your system. Penetration testing is all about
4 Minute 43 Second Read


Michelle Drolet
The threat of a cybercriminal gaining access to your network is a constant source of anxiety. Amid all of the high-profile data breaches, businesses and organizations of all sizes have been successfully targeted by hackers who employ a wide range of different strategies. Too many companies have had to learn all about the potential cost of
4 Minute 32 Second Read


Michelle Drolet
If you don’t have a lot of budget at your disposal, these open-source intrusion detection tools are worth a look. As businesses grapple with the pandemic, millions of workers are no longer working in the traditional office behind the traditional perimeter. They are working from home, accessing data and network resources using unauthorized devices, unauthorized
4 Minute 47 Second Read


Michelle Drolet
Learn from our panel of experts as they discuss Privacy, Security and Compliance and how to effectively navigate the ever-evolving compliance mandates and regulations. – Learn how to make information security actionable.


Michelle Drolet
With ransomware and phishing attacks on the rise, companies must continuously focus on cyber risks to protect assets and customers. Covid-19 forced organizations to evolve their business models overnight. The demand for digital infrastructure has skyrocketed and industries are seeing large-scale adoption of work from home. Unauthorized software, unsecured devices, stressed and distracted workers have
3 Minute 46 Second Read


Michelle Drolet
Many organizations lack the internal expertise to address threat detection and response effectively, but MDR can fill the gap. Part 1 will look at why you should consider MDR to manage your cybersecurity threats. Part 2 will examine what to look for when shopping for MDR services.


Michelle Drolet
Hear from our resident expert as he discusses best practices for cloud-based forensics.


Michelle Drolet
This whitepaper examines the challenges inherent in achieving continuous PCI DSS compliance across multi-cloud and hybrid landscapes and what to look for in evaluating solutions and service providers that can address those complexities.


Michelle Drolet
Unauthorized software and devices and stressed and distracted workers have expanded the attack surface and left businesses exposed to a number of cyber-risks. Small and medium-sized businesses in particular are most vulnerable since a majority of them run legacy or outdated systems.
2 Minute 42 Second Read


Michelle Drolet
Cybersecurity resilience depends on having a detailed, thorough, and tested breach response plan in place. Here’s how to get started. No matter how secure your business, data breaches are an unfortunate fact of life. Whether an attack is the result of a determined cybercriminal, a disgruntled insider, or simple human error, you can limit the
4 Minute 47 Second Read


Michelle Drolet
Per a recent analysis from Microsoft (via The Interpreter), every country in the world has fallen prey to at least one COVID-19-related attack. Homeland Security and the Cybersecurity and Infrastructure Security Agency (CISA) issued an advisory back in issued an advisory back in April…
1 Minute 47 Second Read


Michelle Drolet
Covid-19 has disrupted our lives and caused a lot of stress and panic globally. Even though lockdowns may be relaxing, cyber-attacks are showing no signs of slowing down. The pandemic has created the perfect environment for hacktivists to strike with a high degree of success. Let’s understand the top five reasons for this: 1. Expanding
4 Minute 37 Second Read


Michelle Drolet
As the average monetary cost of a malware attack continues to increase and currently costs an organization an average of $3.86 M, it is vital to be up to date on detection and prevention best practices. No level of investment prevents or blocks 100% of attacks. You will learn how to continuously identify and address
0 Minute 25 Second Read


Michelle Drolet
Many organizations lack the internal expertise to address threat detection and response effectively; MDR can fill the gap. Here’s what to look for when you shop for MDR services. Threat detection and response is a priority for most CISOs because they recognize that the faster a breach is detected and dealt with, the easier and cheaper it is to fix. And since it takes an average of 280 days to identify and contain a breach, according to Ponemon Institute research, there’s plenty of room for improvement.


Michelle Drolet
Per a recent analysis from Microsoft (via The Interpreter), every country in the world has fallen prey to at least one COVID-19-related attack. Homeland Security and the Cybersecurity and Infrastructure Security Agency (CISA) issued an advisory back in April relating to heavy exploitation of Covid-19 by malicious cyber actors. A Breeding Ground For Cybercriminals That’s Not Going
4 Minute 25 Second Read


Michelle Drolet
In a recent article, “New Tech Project? Get Your Devs On Board Fast with These 16 Tips” published on Forbes Technology Council, Michelle Drolet shares how a Solid Secure Development Lifecycle can help: Create a solid SDLC program plan. Developers need a solid secure development life cycle program plan. Test against the plan/program’s “application risk
0 Minute 23 Second Read


Michelle Drolet
Security pros have a lot to juggle, but look in the right places and you can find invaluable assistance for free. Maintaining security is a never-ending business. There’s so much to worry about, from misconfigured software to phishing attacks to a rapidly expanding inventory of devices with their own vulnerabilities and update requirements. We could all use
5 Minute 3 Second Read


Michelle Drolet
Live online Friday, July 10th 12:00 – 1:00 p.m. EST Panelist include: Michelle Drolet, Towerwall & Jason Klein, Offit Kurman The threats are real and increasing daily. Learn how you can protect yourself and your cannabis company from unauthorized access to confidential files and proprietary data. By now, we are all too familiar with the


Michelle Drolet
Live online July 2, 2020 12:00 pm ET Panelist include: Michelle Drolet, Towerwall, Itay Nachum, Safe-T, Scott Tingley, Cogito & Tom Ward, Qnext Data breaches are on the rise, highlighting no organization is safe from cyberattacks. One cause is that workforce mobility and cloud computing has placed most workloads beyond the shelter of corporate networks

Please join us for our 8th Annual Information Security Summit! “The Evolving Threat Landscape 2020” This regional event provides participants with an update on the latest developments, trends, and status in information security. With the growing popularity of disruptive technologies, including mobility and cloud computing, social networking, and big data analytics, the accompanying data security


Michelle Drolet
10) Zooming out. Video conferencing is a two-edged sword; while a boon to nurture group discussion, the degree of focus paid to a small screen while feeling self-conscious (how’s my hair?) can oversaturate users. People are now reporting Zoom fatigue, citing anxiety. Identify mental health and grief counsellors who can step in during these COVID-19
2 Minute 3 Second Read


Michelle Drolet
The COVID-19 pandemic has brought about a seismic shift in how the world goes to work. Apart from essential services, remote work is the new normal, mandated everywhere — even in organizations that never previously offered remote work options. Lack of VPN infrastructure or its ability to scale, legacy systems that were never designed for remote work,
4 Minute 53 Second Read

Michelle Drolet
Live online June 4, 2020 12:00 pm ET Presented by Diana Kelley, Cybersecurity Field CTO, Microsoft Michelle Drolet, CEO, Towerwall Wherever we turn it feels like the news is all COVID-19 all the time. Many of us are feeling stressed and overwhelmed and attackers know it. At Microsoft, we’ve seen an increase in the success
0 Minute 39 Second Read

Michelle Drolet
Live online Thursday, May 28 at 3:30 p.m. ET Cyberthreats morph rapidly as they try to stay ahead of our defenses; wearing new disguises and breaking down virtual barriers in unique ways. The answer to, “How do I remain secure?” changes as quickly as the cyberthreats we face. Join us for an interactive Q&A Panel


Michelle Drolet
These are unprecedented times. As companies scramble for business continuity, millions of workers around the world are forced to adapt to a workplace culture dubbed as the world’s largest work-from-home experiment. But there is a steep price to be paid for this change — weakened cybersecurity. With more and more people working from home, the attack
4 Minute 48 Second Read


Michelle Drolet
10. Pandemic panic Criminals thrive during a crisis, knowing people under stress and distraction are more prone to readily click a text or email link without thought to its legitimacy. As such, COVID-19-related phishing attacks grew 600% in the first quarter. 9. FTC Warnings The Federal Trade Commission just reported $12 million in coronavirus scams calling it the
1 Minute 34 Second Read


Michelle Drolet
10) Start with a plan. Companies of all shapes and sizes should draft a distinct crisis response plan. Existing disaster recovery plans or business continuity plans might not suffice. 9) Lead with leadership. Pick a small team responsible for your plan. Get buy-in from the top, pull in human resources, finance, IT. Develop policies minimizing
1 Minute 57 Second Read


Michelle Drolet
As the novel coronavirus (which causes COVID-19) continues to spread around the world, businesses must do what they can to prepare for absent staff and possible periods of enforced closure. In general, it’s vital that companies of all sizes and types draft a distinct crisis response plan because existing disaster recovery plans or business continuity
4 Minute 50 Second Read


Michelle Drolet
Join our partner Pcysys for their latest webinar: What’s New in PenTera Thursday, March 26th 3:00 PM GMT | 10:00 AM EST In the upcoming What’s New webinar, we’ll go over the new features and enhancements in PenTera version 4.0. You’ll learn about our new: Revamped User Interface Direct Access to Entire Remediation Wiki Web


Michelle Drolet
10) High priority. 64% of businesses are prioritizing IT security above everything else and 80% of small and medium businesses rank IT security as a top business priority. 9) Bad news. A successful cyber-attack can damage your company reputation beyond repair including financial losses, intellectual property theft and erosion of customer confidence and trust. 8)
1 Minute 36 Second Read


Michelle Drolet
As a valued customer, I appreciate the trust you place in your Towerwall team. I want to assure you that the safety and security of our customers and employees is Towerwall’s highest priority. Given the heightened business environment due to the Coronavirus (COVID-19), our top priority is to ensure the continuity of our support services
1 Minute 25 Second Read


Michelle Drolet
When apps are developed in a hurry and not properly put through their paces, the risk of something going wrong is high, as the Iowa Democratic Party just learned to its cost. Creating secure, fully functional mobile apps takes time and requires stringent testing. In the aftermath of the delayed results for Iowa’s Democratic presidential caucuses, it
4 Minute 50 Second Read


Michelle Drolet
As California’s privacy legislation goes into effect, it’s time to take stock of your security strategies around data and think about the future. The trend towards greater privacy is set to continue. The big data grab drove companies to stockpile data, with little thought of how to use it, and even less thought about how
4 Minute 47 Second Read


Michelle Drolet
Is cybersecurity a top priority for your business? We certainly hope so. A recent report revealed that almost 64% of all businesses prioritize IT security above everything else. Even 80% of all SMBs rank IT security as a top business priority. The Impact Of Cybercrime Can Be Far-Reaching A successful cyberattack can damage your company beyond repair. This could
4 Minute 54 Second Read


Michelle Drolet
Cloud security is simpler than you think. Move to the cloud with confidence while increasing the efficiency of your security management, compliance, and governance. Listen in to learn how you can: Secure once and run everywhere: manage a multi-layered security strategy across your data center and cloud from a single console. Secure every cloud and


Michelle Drolet
It may seem like a peculiar twist of irony, but as the technical capabilities afforded by automation proliferate, successful cyberattacks are increasingly more reliant on human execution. Join this 60-minute presentation to learn more about the cyber threat landscape, threat hunting and response techniques, and real-world examples of how Sophos Managed Threat Response detects and


Michelle Drolet
The risk of a data breach is ever-present and can prove disastrous especially for cash-based businesses like cannabis. It’s vital to guard against cyber-attacks, but also to establish solid plans to ensure you react to any breach in the right way. It has never been easier for cybercriminals to infect your business with malware or
4 Minute 44 Second Read


Michelle Drolet
Our CEO, Michelle Drolet recently sat down with Superb Crew to discuss industry trends, threats and how to stay ahead. Link to the full interview below Q: What are you most excited about in the industry at the moment and what future trends are you expecting to see? A: We see more business coming to
0 Minute 46 Second Read


Michelle Drolet
10. Nigerian prince lives. The royalty who wants to send you money is the oldest scam in the book, yet it continues to lure victims. Phishing works by creating false trust to give up log-in credentials, click a bogus URL or download a malware-infected file. 9. Avoid pain. Be aware successful phishing scams can result
1 Minute 41 Second Read


Michelle Drolet
Record numbers for internet sales were reported in 2019, but online retailers aren’t the only ones laughing all the way to the bank. Cybercrime costs retailers a staggering $30 billion a year, and the sector is among the top ones targeted globally. Last year, three quarters of global retailers reported falling victim to cyberattacks. A New Attack Method Emerges: Ad Threats Cyberattackers are
4 Minute 0 Second Read


Michelle Drolet
2019 is set to break a record for the highest number of security incidents ever recorded and probably the biggest and most expensive year in terms of data breach fines, penalties and court settlements. While large-scale breaches always make big headlines, hackers are not sparing small businesses and consumers. As we head into the new decade, cyberattacks will continue
4 Minute 53 Second Read


Michelle Drolet
It’s almost a no-brainer that all organizations, regardless of their size, need some form of cybersecurity. Cybersecurity not only means that you protect your digital assets against a cyberattack, but it also means that you must plan for the inevitable. What if your data is breached or your systems are attacked? Seems pretty obvious, doesn’t
4 Minute 40 Second Read


Michelle Drolet
Enterprise access requirements are growing ever more complex due to application dynamics, cloud adoption and mergers. To cut through this complexity, technical professionals should explore SDP – a new technology whose strength lies in facilitating access to enterprise apps. Safe-T’s Software-Defined Access Suite takes SDP to the next level, revolutionizing Zero Trust network design.


Michelle Drolet
The cloud has revolutionized the way we work. It has become an indispensable part of our lives. It has allowed us to do business in a faster, more scalable way and has become the foundation for other disruptive businesses. Cloud accelerated the fortunes for some of the world’s largest companies. For Google, Microsoft and Amazon, cloud services is one
4 Minute 5 Second Read


Michelle Drolet
Staying abreast of the latest cybersecurity trends can be a tricky challenge for modern businesses, but it’s absolutely vital if you want to safeguard your data. Plugging vulnerabilities, keeping your cloud secure, and avoiding phishing scams and ransomware attacks requires diligence, user awareness, and vigilance.


Michelle Drolet
Forbes Technology Council Is an Invitation-Only Community for Executives Leading Their Industry BOSTON – October 25, 2019 — Michelle Drolet, CEO of Towerwall, is celebrating her one-year anniversary as a member of the Forbes Technology Council, an invitation-only organization for senior leaders to publish original content, connect and excel. “We are so pleased to have
1 Minute 55 Second Read


Michelle Drolet
Companies that move to the cloud have to assume new responsibilities, develop new skill sets and implement new processes. The first step to better cloud security is to assume you have no security. Cloud computing has transformed the way businesses work and continues to disrupt traditional business models. IDC predicts that by 2023 public cloud spending will
3 Minute 49 Second Read


Michelle Drolet
Expert panelists Michelle Drolet of Towerwall and Tom Ward of Qnext/FileFlex joined participants online on October 1st 2019 to speak about how to use a decentralized edge-cloud architecture to secure your company’s files & data and prevent cybersecurity threats and ransomware attacks. Watch the full webinar below:


Michelle Drolet
Our own Michelle Drolet sits down with Jeffrey Davis, founder and host of Radio Entrepreneurs to share her story and lessons learned as an entrepreneur. Watch above or click here to listen > Radio Entrepreneurs shares the stories of entrepreneurs in the interest of giving more exposure to innovative and fast-moving companies while creating a
0 Minute 20 Second Read


Michelle Drolet
One of the biggest challenges about working in cybersecurity is that you’re facing an enemy who learns and adapts. Cybercriminals can be very organized, they cooperate, and they’re constantly working to develop new techniques and strategies that will breach your defenses. They’re also growing increasingly adept at sniffing out the best opportunities to extract maximum
4 Minute 6 Second Read

Thank you to all who attended this year’s Information Security Summit! Please see the video recap below. Looking forward to seeing everyone next year!


Michelle Drolet
How to secure remote file access, sharing and collaboration with decentralized cloud computing. When: Tuesday, October 1, 2019 – 2:00 PM EST Sponsored by: Sponsored by Towerwall and Qnext Presented by: Michelle Drolet, Paul Barker Register now >


Michelle Drolet
Workloads in the public cloud are the new pot of gold for savvy cybercriminals. Often misconfigured and under-secured, they’re an easy way for hackers to steal data and take advantage of your processing power. If you use Amazon Web Services, Microsoft Azure, or Google Cloud Platform, or are thinking about migrating to any of these,


Michelle Drolet
Social media has completely changed the way humans interact. Our lives have become increasingly public as we all share a variety of personal information online on various social networks. 2019 has seen worldwide social media user numbers grow to almost 3.5 billion, with 288 million new users in the past 12 months, pushing the global social
5 Minute 10 Second Read


Michelle Drolet
When we hear the word “cybersecurity” a lot comes to mind — firewalls, antivirus, endpoint protection, email security, web security and much more. But how often do we think or talk about people? This is a central element in cybersecurity that is often ignored. ‘To err is human”— it’s obvious that as humans we often
4 Minute 16 Second Read


Michelle Drolet
While much of cybersecurity is focused on prevention, the simple fact is that many attacks are successful. Even a sophisticated, expensive security system is going to be breached from time to time. Smart attackers try to fly under the radar, biding their time and extracting maximum value or causing maximum carnage, sometimes over a period
4 Minute 36 Second Read


Michelle Drolet
Businesses continue to face modern cyber attacks such as ransomware threats and data breach incidents. In the wake of a non-stop onslaught from advanced hackers, it seems that no matter what defensive measures organizations put in place, cyber adversaries and malware authors are able to circumvent them. Cybercriminals are not only motivated to target high-profile
4 Minute 18 Second Read


Michelle Drolet
When we say “operationalizing cybersecurity,” what we are essentially saying is the implementation of best practices that strengthen your cybersecurity infrastructure. This results in a strong security posture able to address advanced and continuously evolving cyberthreats leveled at any organization. A well-defined cybersecurity strategy lies at the very root of seamless operationalizing. Key stakeholders like
4 Minute 37 Second Read


Michelle Drolet
The numerous high-profile data breaches that took place in 2018 illustrate that no organization, irrespective of size, scale or scope, is immune from cyberattacks. Last year witnessed a 350% increase in ransomware attacks and a 70% increase in spear-phishing attacks. We are looking at a state-of-affairs wherein it is very easy for cybercriminals to exploit security vulnerabilities and target
4 Minute 55 Second Read

7th Annual Information Security Summit Presented by MassBay Community College and Towerwall, Inc. When: June 6, 2019 8:00AM – 1:30PM When: MassBay Community College 50 Oakland Street Wellesley Hills, MA 02481 About the Conference: This year’s Information Security Summit will deliver information on the latest threats and emerging technologies such as ML, AI, and automation.


Michelle Drolet
As cyber attacks become increasingly common, it is vital for organizations to be armed with the most effective tools and knowledge to prevent, detect and respond to cyber threats. Join this interactive Q&A panel with top security experts across the ecosystem to learn more about: Trends in Advanced Threat Detection & Vulnerability Management How to


Michelle Drolet
What is cyber threat intelligence, and how can organizations leverage it to identify threats and potential malicious activity in advance? Discover the best ways organizations can arm themselves with actionable threat intelligence to block cyber attacks or mitigate their impact. Join this panel of experts to learn more about: Cyber threat intelligence: What it is


Michelle Drolet
Cybersecurity, much like safety, cannot be achieved – it is an ongoing process that changes and adjusts to respond to the threat landscape, business needs and resources. As essential a cybersecurity strategy is to the enterprise, so is the implementation of it. Host: Michelle Drolet, CEO, Towerwall and Amy McLaughlin, Director of Information Services, Oregon

Michelle Drolet
What Exactly Is Automated Penetration Testing? Software-based penetration testing is here! Learn how leading companies are taking advantage of this new technology to drive cost-effective remediation. When: Wednesday, February 27th 2:00 PM EST Host: Amitai Ratzon CEO , Pcysys Your Takeaways: A fresh approach to vulnerability remediation prioritization How to ensure your security posture is kept


Michelle Drolet
Best Practices for Protecting Your Business from Cybercrime Cybercrime has evolved from random activities being carried out by individuals into a billion dollar illegal industry that continues to grow. How is cybersecurity keeping up with the rise of cybercrime? Join this panel of security experts to learn more about: Trends in cybercrime and lessons learned

Michelle Drolet
An Introduction to New Technology – Automated Penetration Testing In this webinar, we will review Automated Penetration Testing – principles, benefits, use cases, case studies, and live demo. When: Wednesday, January 16, 2019 2:00 PM ET Your Takeaways Understand the threat actors’ perspective of your company Learn of a different approach to vulnerability remediation prioritization


Michelle Drolet
Ransomware attacks can prove extremely disruptive and expensive to remedy. Prevention is better than finding a cure, and ransomware incidents are easily preventable with the right action. A few high-profile ransomware incidents have spread awareness, and many individuals and organizations have likely taken strides to protect themselves, which may have diminished the success rate of ransomware
4 Minute 48 Second Read

Michelle Drolet
Best Practices for Securing Your Organization in 2019 Data breaches are on the rise and getting their fair share of media attention. It is no longer a question of “if”, but “when” an organization will get breached. So, how are organizations preparing for the inevitable? When: Tuesday, January 15, 2019 11:00 AM ET About the


Michelle Drolet
Bad actors have taken advantage of unpatched systems, software vulnerabilities and increasingly devious forms of malware for years, but their preferred weapon is often phishing. While their motives haven’t changed — luring target victims to click highly legitimate-looking emails so they can steal the keys to the castle — I’ve seen their attack methods grow more sophisticated
4 Minute 55 Second Read

Michelle Drolet
The NIST Cybersecurity Framework (CSF) is a crowdsourced set of best practices to help you analyze your cyber risk posture and work towards improving it. Learn what it can do for your business, how to tailor and implement it, and how to manage it to work towards your desired security posture. The cybersecurity threat and
4 Minute 49 Second Read

Michelle Drolet
The Rise of Targeted Ransomware What is targeted ransomware? Are you susceptible? What can you do to defend against it? Presented by: Michelle Drolet, CEO, Towerwall Watch now >


Michelle Drolet
Dean College’s IT team experienced the challenges of protecting the College’s information and technology assets, complying with regulatory requirements, and adhering to security best practices. This translated into the need to develop a solid foundation and implement policies on secure, responsible, and acceptable use of the College’s information and technology assets, addressing potential phishing and ransomware threats, and building repeatable information security programs…


Michelle Drolet
Breaches often take weeks or even months to uncover, but the right strategy combined with strong endpoint detection & response (EDR) tools can make all the difference. We examine seven vital factors to consider. Many different elements need to come together for an organization to secure its data properly. Most companies adopt a security strategy
4 Minute 35 Second Read

Michelle Drolet
Michelle Drolet sits down with Mindset Entrepreneur. Click the image below to watch now:
0 Minute 4 Second Read


Michelle Drolet
Many organizations take steps to guard against data breaches, employing new policies, tools and strategies that make them feel protected, but their defenses may not be as strong as they think. Unfortunately, this false sense of security is all-too-easy to come by. Data breaches are commonplace now and there’s a growing realization that organizations need
4 Minute 42 Second Read


Michelle Drolet
10) Got cloud? According to Cloud Security Alliance, more than 70 percent of the world’s businesses now operate in some capacity on the cloud. 9) Cloud positive. Running apps in the cloud offers lower fixed costs, auto updates, easier collaboration, disaster recovery, scalability, pay-as-you-go options, lower tech support costs and access from any device. 8)
1 Minute 33 Second Read


Michelle Drolet
Our own Michelle Drolet to sit on panel at Boston’s Town Hall: Cannabis Conversations. We hope to see you there!


Michelle Drolet
Everyone should employ an intrusion detection system (IDS) to monitor their network and flag any suspicious activity or automatically shut down potentially malicious traffic. We look at five of the best open source options. As cybersecurity professionals, we try to prevent attackers from gaining access to our networks but protecting perimeters that have grown exponentially
4 Minute 49 Second Read


Michelle Drolet
As long there is money to be made, cybercriminals will continue to take advantage of our security weakness to pick our pockets! And hackers are a dime a dozen, with lots of tools at their disposal. Check out this Cyber Threat Report, brought to you by Sophos, to learn more about the capitalistic cybercriminal and

Michelle Drolet
Trends in Data Breaches and Comprehensive Responses Does your organization have a data breach response plan? Join Michelle Drolet and a team of industry experts for an interactive Q&A panel and discover the best practices for breach response and how to strengthen your organization’s cyber resilience. About the Webinar Join this interactive Q&A panel with


Michelle Drolet
As cloud adoption soars to new heights, security standards have failed to keep pace. Organizations need to start taking responsibility for their own cloud security and these five practical tips will help. There’s no doubt that widespread adoption of the cloud has enabled collaboration on a much greater scale, driving innovation and creativity. Distributed workforces
4 Minute 18 Second Read


Michelle Drolet
Trends in Data Breaches and Comprehensive Responses Does your organization have a data breach response plan? Join Michelle Drolet and a team of industry experts for an interactive Q&A panel and discover the best practices for breach response and how to strengthen your organization’s cyber resilience. When: Wednesday, September 19, 2018 8:00 AM ET About


Michelle Drolet
Click here to watch the webinar now > Our own Michelle Drolet will be discusses the need for developing a solid Incident Response Program and doing Tabletop exercise throughout the year. An Incident Response Plan (IRP) will ensure information security incidents, once identified, will be handled and communicated appropriately. Consistency of how incidents are handled


Michelle Drolet
Join us for our next InfoSec at Your Services Meetup: “GDPR Context and Myth Busters by Our Resident Expert Greg Albertyn” Hosted by Michelle Drolet and Greg Albertyn When: Thursday, September 6, 2018 6:30 PM to 8:00 PM Where: Skyboxx, 319 Speen Street, Natick We will discuss: How we collect, use and share personal data has


Michelle Drolet
With the CCPA coming hot on the heels of the GDPR it makes sense to get your consumer data management in order. Taking steps to protect all private data today will pay dividends tomorrow. The idea that organizations should be doing more to protect the personal data they hold about individuals has been gaining ground
4 Minute 33 Second Read


Michelle Drolet
ISSA New England Chapter Meeting You are invited to The ISSA New England Chapter’s September Meeting for a morning packed with well-known practitioners in the field of Information Security as well as networking with your peers. Attendees will earn 4 CPEs When: Tuesday, September 25th, 2018 8:00 am – 12:30 pm Where: Boston Children’s Museum


Michelle Drolet
How to Build a Robust Incident Response Capability for Financial Institutions Our own Michelle Drolet will be discussing the need for developing a solid Incident Response Program and doing Tabletop exercise throughout the year. An Incident Response Plan (IRP) will ensure information security incidents, once identified, will be handled and communicated appropriately. Consistency of how


Michelle Drolet
Click Here to Watch the Webinar Now > View the Presentation > About the Webinar Enterprises face an exploding number of unmanaged and IoT devices on their networks, and cyber attacks are increasingly targeting these vulnerable devices. Join Armis and Towerwall to learn about 8 ways that you can secure your enterprise from these


Michelle Drolet
Make sure you understand the need to operationalize data management and security. There has been a widespread rush to get organized and compliant in time for the May 25 deadline when the EU data privacy law General Data Protection Regulation comes into effect. Little wonder when you consider what non-compliance with the GDPR could cost you —
3 Minute 35 Second Read


Michelle Drolet
Are you ready for GDPR? Do you meet the new requirements? Do you know your risk exposure? A lot of companies do not know. To give you an idea of the uncertainty surrounding the Regulation, Vanson Bourne surveyed 1,600 organizations. A staggering 37% of respondents did not know whether their organization needed to comply with GDPR, while 28% believe they did not need to comply at all. This uncertainty will not provide any protection from fines.


Michelle Drolet
6th Annual Information Security Summit Presented by MassBay Community College and Towerwall, Inc. When: Thursday, May 24, 2018 8:00AM – 1:30PM When: MassBay Community College 50 Oakland Street Wellesley Hills, MA 02481 About the Conference: The Information Security Summit is a regional event with the goal to give participants from New England an update on


Michelle Drolet
Our own Michelle Drolet featured in Fierce CEO’s “Special Report Women CEOs on Blazing a Trail to the Top: Part 2” What does it take to reach the chief executive post? Being direct about what you want, for one. “If women want the brass ring, they should try to grab it,” says Jennifer Keough, CEO of
0 Minute 48 Second Read


Michelle Drolet
A look at some options for keeping tabs on your staff and the possible pros and cons. Securing your data in the digital age is very challenging, but it has never been more necessary. We just looked at the hair-raising cost of a data breach in 2018 and we know that employees are often the weakest
3 Minute 54 Second Read


Michelle Drolet
Learn about best practices to combat the threat of ransomware There have been some seriously nasty ransomware attacks in the last few years. From Petya to Wannacry to the SamSam attack on health record company Allscripts just last month, ransomware has been wreaking havoc across the world. Global ransomware damages exceeded $5 billion last year, up from $325 million in
3 Minute 34 Second Read

Michelle Drolet
Click Here to Watch the Webinar Now > About the Webinar The deadline for the new European General Data Protection Regulation (GDPR) is four months away, and it is likely to affect most companies around the world in one way or another – even ones not based in Europe. Join our friends from Sophos


Michelle Drolet
10) Data breaches. Nearly 5 million data records are lost or stolen worldwide every single day, or 58 records every second. According to an IBM report, the average cost of a data breach is $7.3 million. 9) Machine learning will play a bigger role in cybersecurity. Because the battle against cyber criminals moves so rapidly,
1 Minute 28 Second Read


Michelle Drolet
58 data records are stolen every second at an average cost of $141 each. Trading in intellectual property and personal data is so widespread that someone invented a calculator that can estimate the potential harm to your own business. Nearly 5 million data records are lost or stolen worldwide every single day, according to the
3 Minute 43 Second Read


Michelle Drolet
Countdown to GDPR: Get the Competitive Edge Webinar featuring Sophos, Twinstate and Towerwall When: Wednesday, January 24, 2018 12:00 – 1:00 PM EST About the Webinar The deadline for the new European General Data Protection Regulation (GDPR) is four months away, and it is likely to affect most companies around the world in one way


Michelle Drolet
Policies and software are not enough to secure your data, staff must be regularly trained. Your organization might have the most robust security program in the world. You may have stringent policies, and the latest and greatest security software tools. You might think your data is safe, but if your employees don’t have the right
4 Minute 3 Second Read


Michelle Drolet
Towerwall & Darktrace Dinner Seminar Hosted by Towerwall When: Wednesday, January 17, 2018 6:00 PM to 8:00 PM Where: Il Capriccio 888 Main St, Waltham, MA 02453 To Register: Contact Kelley Gallo atkelleyg@towerwall.com About DarkTrace Darktrace is the world’s leading machine learning company for cybersecurity. Created by mathematicians from the University of Cambridge, the Enterprise
0 Minute 34 Second Read


Michelle Drolet
Join us for our next InfoSec at Your Services Meetup: “ARMIS IoT Security” Hosted by Michelle Drolet When: Thursday, January 11, 2018 6:30 PM to 8:00 PM Where: Skyboxx, 319 Speen Street, Natick We will discuss: Internet of Things – IoT – the latest buzzwords conjour up images of toasters and refrigerators being controlled by


Michelle Drolet
It may be possible to glean valuable security insights by monitoring the dark web. Although awareness of the importance of cybersecurity is spreading, the number of successful cyber-attacks continues to grow with every passing year. Globally, almost 1.9 billion data records were compromised in the first half of 2017, up 164% compared to the last
3 Minute 31 Second Read


Michelle Drolet
Skills shortage is making shift to continuous appsec testing challenging. While application security (appsec) is firmly on the radar, most organizations still have a way to go before they can be confident about how secure their apps are. Devops is accelerating the speed of development and, coupled with the shift to the cloud, it’s creating
3 Minute 33 Second Read


Michelle Drolet
Click here to watch our latest webinar from our “Lunch with a vCISO” series >


Michelle Drolet
New challenges and threats will face IT departments in the year ahead. As we stand on the threshold of another year, the war for our cybersecurity rages on. There have been many data breaches in 2017, most notably for Equifax, Verizon, and Kmart. But if you seek a silver lining in the cloud, perhaps you’ll
4 Minute 5 Second Read


Michelle Drolet
Today we’d like to introduce you to Michelle Drolet… Thanks for sharing your story with us Michelle. So, let’s start at the beginning and we can move on from there. As founder of Towerwall, I have to say my proudest moment was when I sold my company and then… I rebought it! I remained active
3 Minute 30 Second Read


Michelle Drolet
Join us for our second live webinar: Second Nature Security: More Secure Networks through Behavior Modification, Security Awareness and Training Wednesday, December 13, 2017 | 12:00 PM EDT – 1:00 PM EDT Join us for a vCISO roundtable discussion featuring: Michelle Drolet, Founder & CEO of Towerwall Greg Neville, vCISO & Sr. Security


Michelle Drolet
The NIST Cybersecurity Framework (CSF) provides a set of computer security policies and guidelines for how organizations can assess and improve their ability to prevent, detect, and respond to cyber-attacks.

Michelle Drolet
Deep learning can be a vital supplementary tool for cybersecurity. The meteoric rise of malware has put us all at risk. We are engaged in a never-ending race with cybercriminals to protect systems, plug gaps, and eradicate vulnerabilities before they can gain access. The front line grows by the day as we share more data and employ
3 Minute 37 Second Read


Michelle Drolet
Coming to a future near you: software code that mutates and evolves. We often talk about computer systems and information security in biological terms. Threats and defenses evolve, viruses run rampant, and machines learn by emulating the neural networks in our brains. Cybersecurity is an endless war between attackers and defenders, just as biology is
3 Minute 32 Second Read


Michelle Drolet
The headline-making Equifax data breach was one of the worst ever. Equifax exposed approximately 143 million consumers, but did not notify any of them. This data breach exposed vital information, such as driver’s license, credit cards, social security numbers, addresses, and birth dates. According to the Ponemon Institute, which conducts independent research on privacy, data
4 Minute 20 Second Read


Michelle Drolet
Why you need to go beyond compliance. Businesses will continue to face a ton of cyber threats, some of which will impact organizations severely enough to require security measures that will reach far beyond compliance. A Ponemon Institute study showed that the average compromised record cost approximately $194 per record. Loss of business due to
3 Minute 9 Second Read


Michelle Drolet
You already know how important it is to be HIPAA compliant. A lot of businesses, including registered marijuana dispensaries, get confused about the requirements, when it comes to dealing with protected health information. It can get a little fuzzy, if you’re not privy to the big picture. The Health Insurance Portability & Accountability Act was
2 Minute 25 Second Read


Michelle Drolet
Thanks to all who joined us at the Worcester Business Journal’s IT Forum. We hope that you found the event informative. The following is some post event information that we thought would be helpful. CLICK HERE to take our event survey. Please take a moment to complete this survey. Your feedback is important to
0 Minute 42 Second Read


Michelle Drolet
Did you know that 74% of employees say their job is more fulfilling when they are provided opportunities to make a positive impact at work? Towerwall is proud to be a sponsor of Foundation for MetroWest’s 2017 Community Leadership Breakfast. The Breakfast is one of MetroWest’s key events of the year: it gives corporate decision makers


Michelle Drolet
Any breach of the General Data Protection Regulation could lead to severe fines. The General Data Protection Regulation (GDPR) went through four years of preparation and debate before being passed by the EU parliament last year. Strict GDPR requirements lay out how companies should process, store, and secure the personal data of EU citizens. The enforcement date
3 Minute 32 Second Read
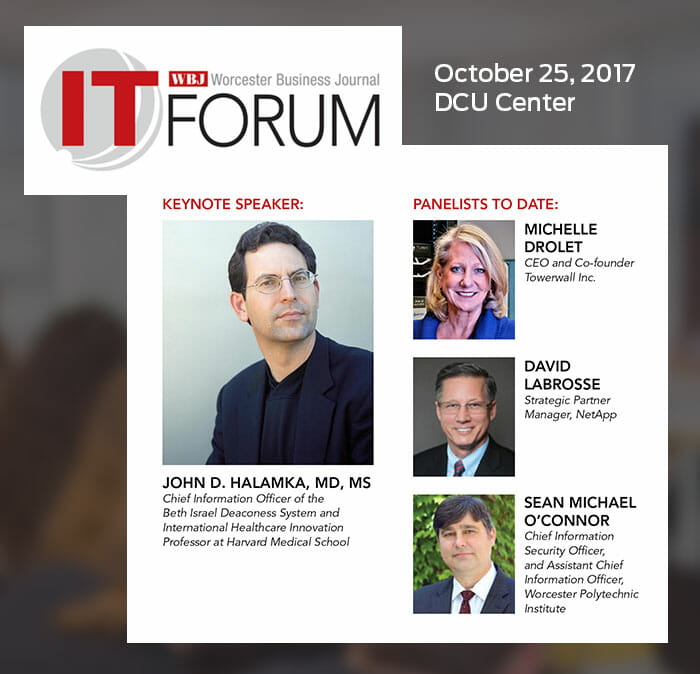

Michelle Drolet
Date: October 25, 2017 Time: 3:00pm-6:30pm Location: DCU Center 50 Foster Street, Worcester Single Ticket Rate: $40.00 Register Today > Please join us and presenting sponsor Echostor and NetApp for this special forum for CIOs, CISOs, CTOs, senior IT leaders and business owners from all industries. Connect and collaborate with some of the area’s top experts on relevant and timely business technology issues and


Michelle Drolet
Happy National Cyber Security Awareness Month! Kick off October with our recent Lunch with a vCISO webinar “Do You Know Your Risk Tolerance – The Role of a vCISO.” Listen Now >


Michelle Drolet
Companies must respond to data breaches properly to limit the damage. Unfortunately, Equifax did not. There have been some very high-profile data breaches in the last few years, but the latest disaster to hit the headlines concerns one of the largest credit bureaus in the United States. It’s estimated that the Equifax data breach exposed 143 million consumers, with
3 Minute 36 Second Read


Michelle Drolet
Join Sophos CEO Kris Hagerman and SVP Dan Schiappa at the Revere Hotel in downtown Boston to learn more about the latest development in Sophos’ innovative approach to endpoint protection. Seating is limited; reserve your seat today to discover: Sophos’ vision on the future of cybersecurity, direct from our CEO and SVP of Products How


Michelle Drolet
Wednesday, October 11, 2017 6:00 PM to 8:00 PM Skyboxx 319 Speen Street, Natick, MA Despite record investments in cyber security technology, the data continues to paint a bleak picture: 91% of breaches start with spear phishing 146 Days – the average time to identify a breach 82 Days – the average time to contain


Michelle Drolet
WELLESLEY HILLS, MA (September 20, 2017) – Massachusetts Bay Community College is pleased to announce it has received a generous donation of $10,000 from this year’s annual Information Security Summit to support student scholarships in the field of cyber security. The Information Security Summit, held each year on MassBay Community College’s Wellesley Hills campus, was
2 Minute 32 Second Read


Michelle Drolet
The need for continuous monitoring, effective metrics and skilled workers. The laudable aim of the National Institute of Standards and Technology (NIST) is to build a common language through a set of best practices and security principles that any organization can apply to combat cybercrime. We’ve looked at what NIST’s Cybersecurity Framework can do for you.
3 Minute 43 Second Read


Michelle Drolet
Each session will provide unprecedented access to the industry’s top Virtual Chief Information Security Officers and cover critical issues in the field. The interactive series will cover a variety of topics, such as aligning information security policies with your firm’s culture and how to prepare for an audit. Attendees will be given the opportunity to


Michelle Drolet
Diving into NIST Special Publication 800-53 for practical advice. We’ve already laid out a broad overview of what NIST’s cybersecurity framework can do for you, so today we’re going to drill into Special Publication 800-53. Published by the National Institute of Standards and Technology, and based on important research from the Information Technology Laboratory, this publication offers
3 Minute 40 Second Read


Michelle Drolet
Medical marijuana, like any controlled substance, requires a strong system of identifying patients properly. As the industry matures, the federal government has increasingly been more involved in enforcing ever more stringent laws and regulations on medical marijuana dispensaries. While it is easy to dismiss this if you’re running your business on a strictly cash-only basis,
4 Minute 18 Second Read


Michelle Drolet
Practical advice to help you build a solid InfoSec plan The risk of your business falling victim to cybercrime has never been higher. Despite a seemingly endless parade of high profile data breaches, ransomware attacks, and phishing scams, many organizations still lack the necessary defenses to identify, prevent, or recover from an attack. The trouble
3 Minute 39 Second Read


Michelle Drolet
Over the last few years we’ve observed the steady rise of ransomware with some trepidation. It is fast becoming a multi-million dollar business, and it’s getting surprisingly sophisticated. The ransomware industry is continually innovating, offering cybercriminals new technology, various business models, and all the support they need to conduct successful attacks on unsuspecting individuals and
3 Minute 38 Second Read


Michelle Drolet
Canna Care Docs is a dynamic company specializing in cannabinoid therapies. Canna Care Docs hired Towerwall to assess their effectiveness in protecting sensitive information such as patient health information and employee personal information from security breaches.


Michelle Drolet
Canna Care Docs is a dynamic company specializing in cannabinoid therapies. Canna Care Docs hired Towerwall to assess their effectiveness in protecting sensitive information such as patient health information and employee personal information from security breaches. Click here to read the Case Study >
0 Minute 13 Second Read


Michelle Drolet
This eBook is a quick start guide for financial institutions who are interested in Banking Cannabis. It covers: the Cannabis Outlook on a national and state level, who is banking cannabis today, the problem with banking cannabis today and how Towerwall can help.

Thanks to all who attended and sponsored our 2017 Information Security Summit. It was a great turnout where we discussed a number of issues and threats facing InfoSec today. We were happy to see attendees share ideas and continue the discussion online with #summitbuzz17 Here are some of the topics discussed at this year’s summit:


Michelle Drolet
10) Always lock your screen. Unlocked phones are always going to dangerously accessible. The first line of defense is a PIN, password, pattern or a biometric measure like your fingerprint. 9) Only install trusted apps. Apps should only ever be installed from official app stores, or your enterprise app store, to reduce the risk of
1 Minute 16 Second Read


Michelle Drolet
Please join us for the The ISSA New England Chapter’s 2017 Sponsor Expo Wednesday, August 2, 2017 from 8:00 AM to 4:30 PM EDT Verizon Labs 60 Sylvan Rd Waltham, MA 02451 You are invited to ISSA, New England Chapter’s Annual Sponsor Expo and Chapter Meeting. Compete in the Security Bee (questions from the CISSP exam)
1 Minute 33 Second Read


Michelle Drolet
We need to make sure the highly regulated world of cannabis business knows how to protect its data, customer and otherwise, yet also control access to it without too much hassle. As an insurgent breed, hackers are savvy and will seek out the path of least resistance. When your defenses are good, the weak link
3 Minute 39 Second Read


Michelle Drolet
“Those within cyber security circles know ransomware has become a lucrative billion dollar business for an army of cybercriminals…It’s time you learn about the tricks and trade of cybercriminals and how their threats are constantly evolving.”– John Shaw, Vice President, Enduser Security Group, Sophos Please join Towerwall and Sophos for an exclusive lunch and learn.


Michelle Drolet
After the recent wave of WannaCry ransomware attacks, managed service providers said the key takeaway they are bringing to customers going forward is the importance of proactive security. “Our whole stance is around proactive security. When you have proactive [security], WannaCry is not going to have an impact,” said Michelle Drolet, CEO of Framingham, Mass.-based
0 Minute 33 Second Read


Michelle Drolet
The legal regime for cannabis is a highly fractured one in the U.S. As of today, we’re approaching the legalized use of either recreational or medicinal marijuana in 30 states with eight states and the District of Columbia nearing full recreational use. Five states in the country continue to ban any use of cannabis, including
3 Minute 40 Second Read


Michelle Drolet
Everything you need to know to stop ransomware. Please join Towerwall and Sophos for an exclusive lunch and learn to learn how to stop ransomware cold. You’ll find out about: Polymorphic Malware What is Next Generation Malware How does a ransomware attack happen? 9 best security practices to apply NOW! June 28, 2017 | 12:00
0 Minute 21 Second Read


Michelle Drolet
BOSTON – May 15, 2017 – Towerwall (www.towerwall.com), a data security services provider for small to mid-size businesses, today announced that CRN®, a brand of The Channel Company, has named Michelle Drolet, Towerwall founder and chief executive officer, to its list of 2017 Power 30 Solution Providers, an elite subset of its prestigious annual Women
2 Minute 49 Second Read


Michelle Drolet
Channel partners can make arguments for the integrated security suite and the best-in-class point product method, but the decision ultimately rests on a customer’s specific needs. “Security is not one-size-fits-all, so it depends on the type of organization and what their risk tolerance level is,” said Michelle Drolet, CEO at Towerwall Inc., a data
0 Minute 26 Second Read


Michelle Drolet
10. Freely hackable Free public Wi-Fi connections are treated like a public utility, but they can be making you vulnerable to hackers. 9. Sign me up By default, most mobile phones/devices are set to ask your permission to join a network. Once you obtain credentials, the known network will join your phone automatically. 8. Sniffing
1 Minute 23 Second Read


Michelle Drolet
Michelle Drolet and the Towerwall team will be attending the 36th Annual New England Bank Technology + Retail Banking Conference and Exhibit, on Friday, May 19th at the DoubleTree in Danvers, MA. Stop by Booth 27 where we will be discussing: FinTech Security Challenges Topics include: Today’s top security threats and how to stay safe Identifying
0 Minute 41 Second Read


Michelle Drolet
User behavior analytics sniffs out anomalies in users’ actions and alerts IT security teams of suspicious behavior The theft of unstructured data is extremely common. It can be very difficult to safeguard emails and files when a lot of people have access. Even the CIA is not immune, judging by the recent exposure of its
3 Minute 40 Second Read


Michelle Drolet
AlienVault recently announced a new addition to the AlienVault training portfolio: Incident Response for USM Appliance Analysts, a two-day course that we will start delivering Live and Online in May. AlienVault has had *many* requests from customers and MSSPs for training focused on the analysis of threats identified by the USM Appliance. This course provides
0 Minute 31 Second Read


Michelle Drolet
Security is taking a backseat as more and more devices connect to the internet The tech world moves at a tremendous pace, unleashing wave after wave of innovation intended to improve our everyday lives. Many new devices, from security cameras to fridges, or TVs to baby monitors, are now internet connected. This affords us remote
3 Minute 40 Second Read


Michelle Drolet
In order to stay ahead of threats, you need to know what to watch out for. This great article: Fraud Speak — Learn the Lingo to Beat Scammers > breaks down and defines hacker lingo. Stay informed, stay ahead, stay safe.
0 Minute 12 Second Read


Michelle Drolet
Join us for our next InfoSec at Your Services Meetup: “7 Secrets of Offensive Security” by Gary Miliefsky When: Thursday, April 6, 2017 6:30 PM to 8:00 PM Where: Skyboxx, 319 Speen Street, Natick Host: Gary Miliefsky Meet Gary > We will discuss: The 7 Secrets of Offensive Security. With all the breaches happening in


Michelle Drolet
Back when Apple was the plucky young upstart that dared to be different, the Mac was the machine for creative types and there was a perception that it wasn’t a target for hackers because of its cultural cool factor. You would expect the same rules to apply to the legalized marijuana market, but a major
0 Minute 46 Second Read


Michelle Drolet
Anatomy of a national point-of-sale breach and takedown of 1,000-plus marijuana dispensaries Back when Apple was the plucky young upstart that dared to be different, the Mac was the machine for creative types and there was a perception that it wasn’t a target for hackers because of its cultural cool factor. You would expect the
3 Minute 50 Second Read


Michelle Drolet
10) Change your password. If you’ve been using the same password for a long time, then it’s time to change it. You should not only change your passwords regularly but not use the same one for every app or website. Try to use more than 13 characters. 9) Turn off wireless connections. When you aren’t
1 Minute 49 Second Read


Michelle Drolet
Cumberland County College invites regional decision-makers to hear Google’s Executive Leadership Coach Steve Vinter and Towerwall’s Michelle Drolet at the college’s 2017 Business Leaders’ Summit. Click here for more information >


Michelle Drolet
What you need to know to defend against targeted attacks. The threat of a targeted attack for any business is real and substantial. It’s vital to ensure that your organization can identify constantly evolving threats, find abnormal and suspicious activity, and take effective action to keep your data safe. Consider that, on average, attackers are
3 Minute 35 Second Read


Michelle Drolet
Click here for more information & to register! Please save the date and plan to join us for this timely forum on what you need to know about the latest security issues, threats, and technologies that will help you protect your business!


Michelle Drolet
10) Adult use A key legislative issue for both opponents and supporters. Only those 21 and over can legally consume, possess and grow marijuana. Some legislators are advocating for a higher age limit. 9) Possession Massachusetts residents can now legally possess up to 10 ounces of marijuana in their primary residence. 8) Growing Massachusetts residents
1 Minute 11 Second Read


Michelle Drolet
Fresh and familiar threats to concern IT departments. As we embark on 2017, it’s time to reflect on a year where cybersecurity has played a major role. Even presidential campaigns haven’t been free from hacking scandals and data leaks. The average cost of a data breach for companies grew from $3.8 million last year to
3 Minute 40 Second Read


Michelle Drolet
Our own Michelle Drolet sits down with tED Magazine to discuss what security measures companies can take to protect their data. Read the full article >
0 Minute 7 Second Read


Michelle Drolet
We need to secure the internet of things. The internet of things (IoT) is all about connecting devices to the internet so that they can talk to each other and to us, to make life more convenient. That might mean turning on the lights when we get up, or allowing us to use our phones
3 Minute 48 Second Read


Michelle Drolet
The Silicon Review has declared SnoopWall is One of the 50 Fastest Growing Tech Companies for 2016. SnoopWall, Inc. delivers breach prevention technology that helps small to medium size enterprises (SMEs) get one step ahead of the next cyber-criminal, malicious insider, phishing attacks, ransomware or zero-day malware behind the corporate firewall. Customer adoption and growth
0 Minute 28 Second Read


Michelle Drolet
Great turnout this year at Worcester Business Journal’s Outstanding Women in Business Awards Our own founder and CEO Michelle Drolet was voted among six other local business leaders as “2016 Outstanding Women in Business” by the Worcester Business Journal. “The winners were selected on their career achievements, ability to transcend both male- and female-dominated professions,
0 Minute 22 Second Read


Michelle Drolet
Join us for our next InfoSec at Your Services Meetup: “Staying on Top of Your Info Sec Game” by Candy Alexander When: Thursday, January 19, 2017 6:30 PM to 8:00 PM Where: Margaritas Mexican Restaurant 725 Cochituate Rd , Framingham, MA Host: Candy Alexander Meet Candy > We will discuss: As you’ve probably heard,


Michelle Drolet
Find out how to prepare for new EU legislation on data collection and security In 2012, the European Commission proposed new regulations on data protection that would supersede the national laws of the 28 EU member states. It was formally approved in April this year, and it will go into effect May 25, 2018. This
3 Minute 35 Second Read


Michelle Drolet
Company among top 20 recognized for their IT security leadership and innovation BOSTON – November 15, 2016 – Towerwall (www.towerwall.com), a data security services provider for small to mid-size businesses, today announced that Cyber Defense Magazine has named Towerwall a “Cyber Security Leader for 2016.” Towerwall was among the top 20 companies to receive the
1 Minute 38 Second Read


Michelle Drolet
The key to securing against this threat lies in a common metaphor—if a ship has a hole, it is better to patch the breach than bail the water Data breaches are increasingly becoming an expensive problem for more and more companies. According to the most recent Ponemon Institute Data Breach report, insecure data cost companies
4 Minute 49 Second Read


Michelle Drolet
Michelle Drolet, CEO of Towerwall in Framingham, is an innovative thinker. Never one to shy away from looking at new factors that come into a situation with an open perspective, she has a few things she’s learned about good management and good leadership along the way. First, she delegates more. “When I first started, it
3 Minute 55 Second Read


Michelle Drolet
The average cost of a data breach involving fewer than 10,000 records was $5 million The American public has become so inured to data breaches that it’s difficult to remember them all. Infamous breaches like the ones at Target and Sony become almost forgettable when confronted with the recently disclosed half-billion accounts compromised at Yahoo
3 Minute 27 Second Read


Michelle Drolet
This year’s winners represent “the best of what professionals in the region can be” BOSTON – October 25, 2016 – Towerwall (www.towerwall.com), a data security services provider for small to mid-size businesses, today announced that its founder and CEO Michelle Drolet was voted among six other local business leaders as “2016 Outstanding Women in Business”
2 Minute 12 Second Read


Michelle Drolet
We are honored to be named a Cyber Security Leader 2016 by Cyber Defense Magazine We are excited to share the list other worth leaders in cyber security. Click here to see the full list of winners. Click here to read the latest edition of Cyber Defense Magazine > For nearly 25 years, our dedicated
0 Minute 28 Second Read


Michelle Drolet
Thank you to all who attended our inaugural InfoSec at Your Services Meetup! We discussed current and emerging issues, best practices and challenges facing information security and cyber security leaders across all industries. Stay tuned for more upcoming InfoSec Meetup events.
0 Minute 12 Second Read


Michelle Drolet
Healthcare providers have always been attractive targets for data breaches. Why? The value of a health record is high. According to Reuters, health records are 10 to 20 times more valuable than credit card numbers. Rather than stealing health records and trying to sell them on the black market, cybercriminals are using ransomware to turn a much quicker profit.


Michelle Drolet
Last week we hosted an informative webinar on today’s ransomware threats with our security partner Sophos. Watch a recording of the webinar below. I am sure you are seeing the explosion of ransomware in the headlines. Businesses of every size are targets and analysts estimate ransomware is on pace to be a $1B/year crime in


Michelle Drolet
10) Nothing hazy about the laws Marijuana (or cannabis) is one of the most highly regulated industries in the world, and Massachusetts has the strictest rules governing its production, retailing, grow, testing and security operations. 9) You can be raided. Marijuana businesses must comply with federal, state, city and county regulations and requirements. Despite medical-use
1 Minute 34 Second Read


Michelle Drolet
Join us for our inaugural InfoSec at Your Services Meetup! When: Wednesday, October 19, 2016 6:30 PM to 8:00 PM Where: Margaritas Mexican Restaurant 725 Cochituate Rd , Framingham, MA We will discuss: Risk Communication Strategy – This biggest risk is the uncommunicated one. Hoarding knowledge doesn’t make you the smartest person in the


Michelle Drolet
Check out one of the upcoming complimentary partner webinars: Brute Force Attacks: Keeping the Bots at Bay with AlienVault USM Tuesday, October 11th 10:00am CST / 4:00 PM BST Hosted by AlienVault Brute force attacks are relatively simple for attackers to implement and they can wreak havoc on your organization if you don’t detect


Michelle Drolet
Stay vigilant, plan your response and test your defenses with CIS Controls 18, 19 and 20 This is the final entry in our series on the 20 Critical Security Controls devised by the Center for Internet Security (CIS) as best practices to help the public and private sectors tighten their cybersecurity. We started down the
3 Minute 54 Second Read


Michelle Drolet
Wednesday, October 12, 2016 11:00 AM – 12:00 PM EDT Hosted by Towerwall and Sophos I am sure you are seeing the explosion of ransomware in the headlines. Businesses of every size are targets and analysts estimate ransomware is on pace to be a $1B/year crime in 2016. Sophos Intercept X is their newly released


Michelle Drolet
We are honored to share that our blog was named as a Top Computer Security Blogs 2016 by CreditDonkey. CreditDonkey sites: “Business owners who want the latest information on the world of digital security will appreciate this blog’s straightforward approach to news and advice.” We are excited to share the list with some of our security
0 Minute 31 Second Read


Michelle Drolet
The NSA should disclose all zero-day exploits. But it doesn’t. To say the National Security Agency (NSA) prefers to lay low and shuns the limelight is an understatement. One joke said about the secretive group, widely regarded as the most skilled state-sponsored hackers in the world, is NSA actually stands for “No Such Agency.” But
3 Minute 49 Second Read


Michelle Drolet
WELLESLEY HILLS, MA (August 2016) – Massachusetts Bay Community College is pleased to announce it has received a generous donation of $5,000 from this year’s annual Information Security Summit to support student scholarships in the field of cyber security. The Information Security Summit, held each year on MassBay Community College’s Wellesley Hills campus, was established
2 Minute 21 Second Read


Michelle Drolet
With all the breaches happening in the news, isn’t it time you get one step ahead of the next threat? Get proactive and learn these secrets before you become the next victim.


Michelle Drolet
When is the right time to rent yourself a CISO? The enterprise is facing a dangerous combination of mounting cybersecurity threats of increasing subtlety—and a widening gap in the skills required to identify and combat them. Having someone who knows how to lead the charge in identifying and analyzing threats, creating strategic security plans and
4 Minute 3 Second Read


Michelle Drolet
7 Secrets of Offensive Security Please join us for a complimentary Lunch & Learn session. Tuesday, August 16 11:00 am – 1:00 pm EST Sheraton Framingham Hotel, Framingham, MA *EARN CPE CREDITS In this session you will learn: The 7 Secrets of O ensive Security. With all the breaches happening in the news, isn’t it time


Michelle Drolet
Stay on top of account management and assess staff security skills with CIS Controls 16 and 17 You can have the most secure system in the world, but hackers will always seek out the path of least resistance. When your defenses are good, the weak link is often your employees. Data breaches are most likely
3 Minute 43 Second Read


Michelle Drolet
OXFORD, U.K., July 19, 2016 – Sophos (LSE: SOPH), a global leader in network and endpoint security, today announced Sophos SafeGuard Encryption 8, a new synchronized encryption solution that protects data against theft from malware, attackers or accidental leaks. All organizations can now choose to adopt the best practice of “always-on” file-level encryption to protect
0 Minute 54 Second Read


Michelle Drolet
Ensuring overall compliance with strict regulations is the next growth opportunity. Whatever you think of it, marijuana is here to stay and coming to full legalization in a state nearest you. Controversy follows cannabis into every branch of society: political, cultural, science, health, education, legal and finance. A quick search on YouTube will show heartbreaking
5 Minute 9 Second Read


Michelle Drolet
Towerwall & SnoopWall Complimentary Webinar: Breach Prevention & Near-Term ROI Tuesday, July 26 11:00am – 12:00pm EST Register Now > Today’s hyper-aggressive cyber landscape finds 40% of organizations are breached and the threat of regulatory and compliance fines are impacting productivity and business operations. 95% of these breaches occur behind firewalls on antivirus protected endpoints.


Michelle Drolet
Thanks to all who attended and sponsored our 2016 Information Security Summit. It was a great turnout where we discussed a number of issues and threats facing infosec today. We were happy to see attendees share ideas and continue the discussion online with #summitbuzz16 Here are some of the topics discussed at this year’s summit:
2 Minute 34 Second Read


Michelle Drolet
Failing to take basic security precautions with website passwords puts your data at risk Do you remember back in 2012 when LinkedIn was hacked? Around 6.5 million user passwords were posted on a Russian blog. There was a mandatory password reset for affected users, and LinkedIn released a statement advising people to enable two-step verification
3 Minute 32 Second Read


Michelle Drolet
Make sure the Internet of Things isn’t a route for hackers to get into your home or workplace As more and more Internet-connected devices find their way into our homes and businesses, it’s important to remember that they represent a security risk. The Internet of Things (IoT) is growing rapidly, and in the rush for
3 Minute 48 Second Read


Michelle Drolet
Higher education institutions are a prime target for cybercriminals, and IT needs resources to prevent attacks and provide a proper level of security No industry or sector is immune to data breaches, but some are targeted more often than others. Education came ahead of government, retail and financial sectors, and it was second only to
3 Minute 42 Second Read


Michelle Drolet
Your company’s data is its crown jewels, and you must protect it all times. CIS Controls 13, 14 and 15 will help you. Earlier we delved into disaster recovery and network security. Now it’s time to take a look at Critical Security Controls 13, 14 and 15, which cover data protection and access control. The Critical
3 Minute 50 Second Read


Michelle Drolet
We will be attending, sponsoring and hosting the following InfoSec events this Spring / Summer. Join us! Security BSides Boston 2016 Saturday, May 21 2016 Security BSides is the first grass roots, DIY, open security conference in the world! Security BSides is a great combination of two event styles: structured anchor events and grass-roots


Michelle Drolet
10. Backup files every night. If you can access yesterday’s files, then there is no need to pay to unlock them today. 9. Patch automatically. Make sure operating systems software on all devices (phones, tablets, laptops) and browsers are patched automatically with security updates. 8. Update software. Make sure your endpoints and network devices are
1 Minute 14 Second Read

Michelle Drolet
Is your organization safe from all these connected devices? Wearables are rapidly invading the workplace in much the same way that smartphones did. Fitness trackers, smartwatches, head-mounted displays and other new form factors are beginning to capture the public imagination. Sales of wearable electronic devices topped 232 million in 2015, and Gartner forecasts they’ll rise
3 Minute 48 Second Read


Michelle Drolet
How security researchers and programmers hunt software bugs for cash rewards The business of bug hunting is a potentially lucrative one for both seasoned security researchers and amateurs with an interest in hacking. It’s an area that’s gaining legitimacy thanks to official bug bounty programs and hacking contests, but there’s still a seedy underbelly that
4 Minute 1 Second Read


Michelle Drolet
Watch out for April Fools scamming on Friday by Kevin Frey Annually, businesses and organizations often put up jokes or pranks for April Fools’ Day. Google, Starbucks, Amazon, etc. are frequent participants. E.g. Last year, Amazon revamped their site to look their old, original 1999 version… and Google (known for multiples) turned its “Maps” app
2 Minute 21 Second Read


Michelle Drolet
Complacency in addressing known vulnerabilities puts users at risk If you have even a passing interest in security vulnerabilities, there’s no chance that you missed the news about the DROWN vulnerability. It’s one of the biggest vulnerabilities to hit since Heartbleed, potentially impacting a third of all HTTPS websites. By exploiting the obsolete SSLv2 protocol,
3 Minute 6 Second Read


Michelle Drolet
According to Cisco’s 2015 Annual Security Report, 91 percent of companies have an executive with direct responsibility for security, but only 29 percent of them have a Chief Information Security Officer. The enterprise is facing a dangerous combination of mounting cybersecurity threats of increasing subtlety, and a widening gap in the skills required to identify
0 Minute 31 Second Read


Michelle Drolet
Click here for more information & to register! Please save the date and plan to join us for this timely forum on what you need to know about the latest security issues, threats, and technologies that will help you protect your business!


Michelle Drolet
WASHINGTON – The Internal Revenue Service today issued an alert to payroll and human resources professionals to beware of an emerging phishing email scheme that purports to be from company executives and requests personal information on employees. The IRS has learned this scheme part of the surge in phishing emails seen this year already has
2 Minute 30 Second Read


Michelle Drolet
Security researchers reveal new technique to break TLS using SSLv2 server. The war to close down security vulnerabilities is never-ending, but the new “DROWN” vulnerability is one of the biggest to rear its ugly head in recent months. A group of security researchers from a number of different universities and research institutes just unveiled this
3 Minute 11 Second Read


Michelle Drolet
Following the Center for Internet Security’s best practices. We discussed building malware defenses the last time out, but today we’re going to focus on Critical Security Controls 10, 11, and 12 covering data recovery, secure network configuration, and boundary defense. It’s unrealistic to think that you can completely avoid cyberattacks and data breaches, so it’s
3 Minute 40 Second Read


Michelle Drolet
Privacy and data protection issues confront all organizations—whether you handle employee information, credit card data, sensitive financial information, or trade secrets. Securing data is a daunting task that is further complicated by cross-border transfer issues and the differences in privacy laws around the world. The team at BakerHostetler has developed a prompt and practical PDF
0 Minute 21 Second Read


Michelle Drolet
10. A hedge against a breach A virtual chief information security officer can serve as security consul or as an interim CISO to fill the gaps during a planned information-technology security policy review. Better to be safe than sorry. 9. High talent at low costs As a temp hire, a vCISO offers flexibility and cost
1 Minute 49 Second Read


Michelle Drolet
As threats evolve and grow more sophisticated, securing IT systems is more important than ever. We may welcome in the New Year with open arms, but we must also prepare for the cybersecurity threats ahead of us. The 2015 Cost of Data Breach Study from IBM and the Ponemon Institute put the average cost of
3 Minute 42 Second Read


Michelle Drolet
Ransomware-as-a-service, help desks, third parties — all point to a mature yet illegal enterprise undergoing serious growth. Here are tips to protect yourself and your company. Ransomware is big business. Over the last few years we’ve observed the steady rise of ransomware, with some trepidation. It is fast becoming a multi-billion dollar business, and it’s
3 Minute 49 Second Read


Michelle Drolet
Friday, May 20 2016 (Training) Saturday, May 21 2016 (Conference) Follow BSidesBoston on Twitter: #BSidesBOS @BsidesBoston @MicrosoftNERD Questions: help@bsidesboston.org When: Friday, May 20th, 2016, TBD (Training)Saturday, May 21st, 2016, 9am – 6pm (Conference) Saturday, May 21st, 2016, 9am – 6pm (Conference) Where: Microsoft NERD, 1 Memorial Drive, Cambridge, MA Hotel Room Block: TBD Cost: $20 (This


Michelle Drolet
Online security trends continue to evolve. This year, online extortion will become more prevalent. We also expect that at least one consumer-grade IoT smart device failure will be lethal. Ransomware will make further inroads, since the majority go unreported. China will drive mobile malware growth to 20M, and cybercrime legislation will take a significant step
3 Minute 16 Second Read


Michelle Drolet
10. Everything is connected. As the Internet of Things adds more and more devices to our networks, it creates more doors and windows for cyber criminals. Keep them locked. 9. Ransomware is on the rise. If you don’t want to end up paying to access your own data, then make sure that you protect it
1 Minute 40 Second Read

The ISSA of New England’s 2nd annual virtual chapter meeting will be on: Thursday, January 21 at 12:00 Noon. ( Yes, while you eat lunch you can join us online. ) Careers in Cyber Security is the theme of this meeting. The most pressing problem in security is for sure the lack of qualified people


Michelle Drolet
Hacking and data breaches weren’t just the norm, but they reached far and wide, hitting victims of all kinds, from regular consumers, to government employees, and even children and cheaters. It seemed like no one was spared. The Worst Hacks of 2015…drum roll please! Israel Government Allegedly Hacks Kaspersky Lab The Massive Breach at OPM,
0 Minute 34 Second Read


Michelle Drolet
A “ransomware” segment was recently on NBC’s Today featuring our security partner Sophos. To learn more about ransomware. click the thumbnail below:
0 Minute 7 Second Read


Michelle Drolet
Another staple in a series examining the Center for Internet Security’s best practices. Our last article looked at applying Critical Security Controls 4, 5, and 6 to your organization, covering vulnerability assessment, administrative privileges, and audit logs. Now it’s time to move on to CSCs 7, 8, and 9. Email programs and web browsers are
3 Minute 32 Second Read


Michelle Drolet
The last time we looked at how Critical Security Controls (CSC) can help you build your InfoSec framework, we covered getting a handle on your software and your hardware inventories. Today, we’re going to discuss the importance of continually assessing and remediating vulnerabilities, keeping a tight control of administrative privileges, and monitoring your audit logs.
3 Minute 33 Second Read


Michelle Drolet
Originally posted on MetroWest Daily News. Towerwall, a Framingham-based network security and policy management company, donated $7,000 to the MassBay Foundation to sponsor student scholarships. Towerwall CEO Michelle Drolet, who is also a board member of the MassBay Foundation, presented MassBay interim president Yves Salomon-Fernandez, MassBay chief information officer Michael Lyons and MassBay vice president
0 Minute 42 Second Read


Michelle Drolet
How can you make sure the mobile apps you access are secure? A security profile should be at the top of the developer’s list when compiling a mobile app but that’s hardly the case. That’s a pity, because building a profile is easier to do during the dev phase. Are most mobile apps putting your
2 Minute 41 Second Read


Michelle Drolet
Vendors and other third parties should be treated with the same level of intense scrutiny as your own in-house risk compliance mandates. How seriously is your company treating the risk of a data breach? Have you done due diligence on all of your vendors and third-party partners? Cyberattacks can have a devastating impact in terms
4 Minute 8 Second Read


Michelle Drolet
by Sarah Kuranda Sophos is launching a new technology Monday that synchronizes threat intelligence and automation across endpoint and network levels. Sophos Security Heartbeat, part of the Oxford, England-based company’s new XG firewall series, links together the company’s next-generation firewall and UTM solutions with its next-generation endpoint technologies. In doing that, the company said, it is
3 Minute 12 Second Read


Michelle Drolet
When it comes to infosec, many of the most core basics are being overlooked. Many of the most obvious areas where security can be tightened up with little effort are being blatantly ignored. Are you doing your level best by covering the basics? Below are seven potential vulnerabilities. Most of these can be tackled without
3 Minute 25 Second Read


Michelle Drolet
Critical Security Controls is a set of best practices devised by the Center for Internet Security, a nonprofit dedicated to improving cybersecurity in the public and private sectors. Cyberattacks are costing businesses between $400 billion and $500 billion per year, depending on which analysts you listen to. Cybersecurity has never been a hotter topic. The
3 Minute 49 Second Read


Michelle Drolet
The Enterprise is at risk from malware and vulnerabilities hiding within mobile apps. You have to test your mobile apps to preserve your security. Mobile apps are ubiquitous now, and they offer a range of business benefits, but they also represent one of the most serious security risks ever to face the enterprise. The mixing
3 Minute 44 Second Read


Michelle Drolet
Encryption has a bad rap and far too often protection schemes are deployed foolishly without encryption in hopes of protecting data. t’s a heartache, nothing but a heartache. Hits you when it’s too late, hits you when you’re down. It’s a fools’ game, nothing but a fool’s game. Standing in the cold rain, feeling like
3 Minute 44 Second Read


Michelle Drolet
Encrypting data on your own might be the smartest move. For those of you old enough to remember the TV comedy series “Get Smart” featuring a spy that used his shoe for a phone, the good guys belonged to an agency called “Control,” and the bad guys were affiliated with “Chaos.” This month “Get Smart”
3 Minute 14 Second Read


Michelle Drolet
10. You need a WISP. A written information security policy, or WISP, is vital. Make sure there’s a person in charge of enforcing it. 9. Always encrypt data. Sensitive data, especially personally identifiable information, must be encrypted at all times, from the server, to the cloud, to a laptop or USB drive. 8. Check your
1 Minute 20 Second Read


Michelle Drolet
Non-compliance is a risk, and the Attorney General’s office carries a big stick for those who don’t follow the rules. If you don’t have a written information security program (WISP) in place for your business, then you could be risking data theft, legal action, and punitive fines. The law in many states now dictates that
3 Minute 55 Second Read


Michelle Drolet
The “Stagefright” hole in Android – what you need to know Provided by Paul Ducklin at Sophos, Inc. The conference circuit can be a competitive arena, especially when there are multiple parallel streams. For example, back in 2010, I was at Black Hat in Las Vegas, and I attended the talk next door to the late Barnaby Jack’s now legendary
5 Minute 22 Second Read


Michelle Drolet
Join us at the the Fall meeting of the ISSA of New England on: Thursday, September 17, 2015 11:00 AM to 3:30 PM @Showcase Cinema de Lux at Patriot Place – Gillette Stadium, Route 1, Foxborough, MA Click here for more information on the ISSA, Speakers and Keynote topics Click here to Register About ISSA


Michelle Drolet
Are you patching quickly enough? How safe is the software you use? Do you have a system in place to identify vulnerabilities and patch them when they are discovered? How quickly do you react to vulnerability reports? There’s evidence that software vulnerabilities are on the rise, and few companies are taking the necessary action to
3 Minute 10 Second Read


Michelle Drolet
Cybersecurity is only as strong as the weakest link. If your organization is using third-party vendors, policing their activity is critical to cybersecurity. Few can forget the theft of 110 million customer credit cards from Target in December 2013. But not as many know how hackers gained access to such a vast amount of sensitive
3 Minute 45 Second Read


Michelle Drolet
Falling victim to a ransomware attack is most definitely inconvenient, but it could also serve as a wake-up call to the importance of backing up important data. You’re minding your own business, sitting at your office computer. Suddenly, a pop-up appears – with the logo of the FBI – warning that you’re under investigation for
4 Minute 26 Second Read


Michelle Drolet
Once again, the Information Security Summit hosted by Towerwall and MassBay was a resounding success. Hundreds of attendees and vendors participated in diverse data security panels and networked with industry leaders and peers. The Summit opened with Michelle Drolet, CEO of Towerwall, and Shamsi Moussav, Computer Science Professor at MassBay Community College, presenting scholarships to
1 Minute 31 Second Read


Michelle Drolet
The enterprise is facing a dangerous combination of mounting cybersecurity threats of increasing subtlety, and a widening gap in the skills required to identify and combat them. Having someone that knows how to lead the charge in identifying and analyzing threats, creating strategic security plans and ensuring compliance, requires the right level of expertise. Many
3 Minute 43 Second Read


Michelle Drolet
Is Android secure enough for the enterprise? Android has a bad reputation when it comes to security, which is unfortunate because it’s the biggest mobile platform around in terms of market share. Gartner says Android claimed 80.7% of the worldwide smartphone market in 2014. We know that the BYOD trend has sparked a dramatic rise in personal mobile
4 Minute 13 Second Read


Michelle Drolet
For all the infosec hurdles to overcome, we can build a bright future if the enterprise can pull together. We often talk about the enormous challenges facing IT departments around the world. The consumerization of IT, driven by the BYOD trend and coupled with mobility, has given birth to a wide range of serious security
3 Minute 40 Second Read


Michelle Drolet
From unencrypted email to open Wi-Fi to faulty firewalls, some of the most common security threats could easily give away the entire farm. More threats emerge for IT departments every year. Cybersecurity is increasingly challenging as attacks get more sophisticated. But many core basics are still being ignored. Verizon’s 2015 Data Breach Investigations Report put
4 Minute 22 Second Read


Michelle Drolet
Teaching the workforce to create a heightened state of awareness. It’s time for the business world to toughen up on security. The threat from cybercriminals is pervasive. Successful attacks on financial institutions, large retailers, and even government bodies, are all too common. There’s a reason that the Worldwide Threat Assessment of the US Intelligence Community
3 Minute 34 Second Read


Michelle Drolet
Towerwall Founder and CEO Michelle Drolet’s latest article “Secure Your Future with a Virtual CISO” is featured in the Infosecurity Magazine. Read more below: The enterprise is facing a dangerous combination of mounting cybersecurity threats of increasing subtlety and a widening
2 Minute 27 Second Read


Michelle Drolet
Towerwall Founder and CEO Michelle Drolet’s latest article “Secure Your Future with a Virtual CISO” is featured in the Infosecurity Magazine. Read more below: The enterprise is facing a dangerous combination of mounting cybersecurity threats of increasing subtlety and a widening gap in the skills required to identify and combat them. Knowing how to lead the charge
1 Minute 39 Second Read


Michelle Drolet
Cyber risk report cites server misconfigurations as the No. 1 vulnerability. It’s often said, “There’s nothing new under the sun.” And that appears to be the case in the world of cybersecurity where hackers most often exploit known vulnerabilities to gain access to private computer files, according to HP’s 2015 Cyber Risk Report. Maintaining strong computer security,
2 Minute 26 Second Read


Michelle Drolet
Towerwall Founder and CEO Michelle Drolet’s latest article “Know When to Onboard a Virtual CISO” is featured in the Web Security Journal. Read more below: A virtual Chief Information Security Officer (CISO) can be an invaluable asset to your company. The virtual CISO provides your business with a person who will be in charge of the electronic
1 Minute 19 Second Read


Michelle Drolet
Frequently, companies don’t realize that the mobile apps they use are reason for concern. Once their data is breached, they begin to investigate. However, there are telltale signs that indicate an insecure mobile app. If you know what to look for, you may be able to avoid a catastrophic data breach. Mobile apps are everywhere
3 Minute 2 Second Read


Michelle Drolet
Tips for your third-party risk management program “Home Depot said the crooks initially broke in using credentials stolen from a third-party vendor […] Recall that the Target breach also started with a hacked vendor…” — Brian Krebs, Krebs on Security In everyday business, a complex set of external relationships is commonplace. Services, infrastructure, and
3 Minute 39 Second Read


Michelle Drolet
The US Federal Communications Commission (FCC) on Thursday lay down 400 pages worth of details on how it plans to regulate broadband providers as a public utility. These are the rules – and their legal justifications – meant to protect net neutrality. They were passed last month, and details have been eagerly anticipated. The main gist of the lengthy document
5 Minute 40 Second Read


Michelle Drolet
Our Michelle Drolet is quoted in TechTarget’s article “Four ways DevOps can boost AWS security“. Read more below: Many IT teams believe security belongs to someone else. Building security into the DevOps process can be a tricky but rewarding move. Combine the “It’s not my job” belief that many IT administrators have about security tasks
0 Minute 32 Second Read


Michelle Drolet
Four ways to implement and maintain security testing. Cybercriminals had a fantastic time in 2014 – breaching major retailers such as Home Depot and Kmart, major financial institutions (notably JPMorgan Chase), and a slew of smaller companies. Indeed, cybercrimes are growing more common, more costly, and taking longer to resolve. Those are among the key findings
3 Minute 39 Second Read


Michelle Drolet
Towerwall is proud to offer our new vCISO Program. Introducing Towerwall’s vCISO Program, our unique approach to Virtual CISO. Offering three distinct partner options, our vCISO solutions are tailor fit to your organization’s security needs. Recognizing many small and mid-sized companies have security concerns, yet do not warrant a full-time position, the Towerwall vCISO Platform
0 Minute 33 Second Read


Michelle Drolet
secuProvided by William Gallagher Associates Insurance Brokers, Inc. News broke last week that Anthem, the nation’s second-largest health insurance carrier, was the victim of a data breach by external hackers. This breach affects both current and potentially former clients of Anthem. WGA is monitoring the situation on an ongoing basis, and here is what we
1 Minute 38 Second Read


Michelle Drolet
Towerwall Founder and CEO Michelle Drolet’s latest article “Bridging the Cybersecurity Skills Gap: 3 Big Steps” is featured in the InformationWeek Dark Reading. Read more below: The stakes are high. Establishing clear pathways into the industry, standardizing jobs, and assessing skills will require industry-wide consensus and earnest collaboration. There is a dangerous dearth of qualified Information
1 Minute 7 Second Read


Michelle Drolet
Our Michelle Drolet is quoted in NetworkWorld’s article “Are mobile apps putting your data at risk?“. Read more below: Quite often, companies don’t realize that the mobile apps they use are reason for concern. Once their data is breached, they begin to investigate. However, there are telltale signs that indicate an insecure mobile app. If you know
0 Minute 51 Second Read


Michelle Drolet
The funkily-named bug of the week is GHOST. Its official moniker is the less catchy CVE-2015-0235, and it’s a vulnerability caused by a buffer overflow in a system library that is used in many, if not most, Linux distributions. A buffer overflow is where you assume, for example, that when you handle a four-byte network number written out as
3 Minute 41 Second Read


Michelle Drolet
Please save the date and plan to join us for this timely forum on what you need to know about the latest security issues, threats, and technologies that will help you protect your business! June 4, 2015 8:00AM – 1:00PM MassBay Community College 50 Oakland Street | Wellesley Hills, MA 02481 Pre-registration required. Join us


Michelle Drolet
Anthem, the nation’s second-largest health insurance company, is the latest target of a security breach. Eighty million customers, including the company’s own CEO, are at risk of having their personal information stolen. VPC SAN FRANCISCO – As many as 80 million customers of the nation’s second-largest health insurance company, Anthem Inc., have had their account information


Michelle Drolet
As the International Consumer Electronice Show (CES) 2015 brings forth the next generation of devices to watch out for, it also opens issues of digital security. While new technologies and devices are always interesting, they also have the potential to burn consumers and vendors with risks to security and privacy. With these in mind, we picked
4 Minute 25 Second Read


Michelle Drolet
Our Michelle Drolet is quoted in NetworkWorld’s article “Throw your vendor under the bus after a breach? Not quite so fast“. Read more below: In everyday business, a complex set of external relationships is commonplace. Services, infrastructure, and even software live in the cloud, supplied by third parties. An organization’s value is often in the data it
0 Minute 51 Second Read


Michelle Drolet
As we approach the end of the year, let’s have a look back at the top hacking incidents of 2014. This year, we might have witnessed the most damaging attack of the decade. It will not be easy beating the Sony attack. SONY On November 24th all of Sony Pictures employees’ computer screens started showing a


Michelle Drolet
Sophos Researcher James Wyke recently did an analysis of the malware Vawtrak. He found that Vawtrak has been targeting financial institutions, especially banks. Vawtrak injects a DLL code into the targeted bank’s website, which allows a bypass of the victim’s two-factor authentication and infects the victim with a mobile malware. The malware then automatically transfers
0 Minute 38 Second Read


Michelle Drolet
Sophos Researcher James Wyke recently did an analysis of the malware Vawtrak. He found that Vawtrak has been targeting financial institutions, especially banks. Vawtrak injects a DLL code into the targeted bank’s website, which allows a bypass of the victim’s two-factor authentication and infects the victim with a mobile malware. The malware then automatically transfers
0 Minute 38 Second Read


Michelle Drolet
Building a solid security program takes time. Every organization is different. It’s very important to assess your technology, and consider both internal and external threats. An assessment will reveal vulnerabilities. The remediation process will help you take full advantage of your existing security assets and point you at any gaps that need filling. Even once
3 Minute 33 Second Read


Michelle Drolet
The information security profession, which evolved largely in reaction to threats, is now paying the price of an entire “missing generation.” Companies are challenged finding pros with the combination of business and technical savvy that is needed to combat growing threats. Compounding this problem, educational institutions are not graduating enough students with the necessary skills
3 Minute 3 Second Read


Michelle Drolet
The rise of malware seems to have passed some people by. As the ranks of cybercriminals grow and they find new ways to exploit our systems and steal our data, a lot of computer users and small-business owners have convinced themselves that it won’t happen to them. Here are five common excuses that explain why
2 Minute 44 Second Read


Michelle Drolet
by Mark Stockley This quick fix will show you how to clear out cookies and the cookie-like things that can be used to track you online. If you already know what cookies are all about then you can skip the next bit and go straight to the instructions. Why cookies are important Cookies are very small
7 Minute 0 Second Read


Michelle Drolet
Integrate security testing into your dev process now or else face cyber-attacks later The way we develop software has been radically transformed in the last few years. Agility and speed are vital components for any company that wants to compete in the market. In order to achieve that it has proven necessary to break down
4 Minute 0 Second Read


Michelle Drolet
3 ways to make your Outlook.com account safer by John Hawes Following on from our detailed guide to securing your webmail, here’s a quick breakdown of how to make the most important fixes for users of Microsoft’s Outlook.com (formerly known as Hotmail and, for a while, Windows Live Hotmail). Controls affecting Outlook.com security are mainly found in
4 Minute 49 Second Read


Michelle Drolet
We are proud to announce that our own Candy Alexander will receive the ISSA “Hall of Fame” Award. See below for more information: Honoree to be Recognized Among RSA Founders at ISSA International Conference on Oct. 22 in Orlando BOSTON, MA–(Marketwired – Oct 9, 2014) – Towerwall (www.towerwall.com), an IT security services provider for small
2 Minute 36 Second Read


Michelle Drolet
Check out this infographic for the numbers behind BYOD.
0 Minute 2 Second Read


Michelle Drolet
By: Solange_Desc1 Security researchers have discovered a new software bug known as the “Bash Bug” or “Shellshock,” or to those more technically “in-the-know” as GNU Bash Remote Code Execution Vulnerability (CVE-2014-6271)(link is external). This bug, more correctly termed, ‘vulnerability’, potentially allows attackers to gain control over targeted computers. The bug is present in a piece of computer
4 Minute 10 Second Read


Michelle Drolet
by Paul Ducklin on September 3, 2014 Yesterday was Firefox’s most recent Fortytwosday(updates come out every 42 days, on Tuesdays, in a nod to Douglas Adams), bringing us to Firefox 32.0. For those who like to keep their feature set behind the leading edge, yet stay on top of security fixes, there’s also ESR 24.8 and ESR 31.1. ESR is short for Extended Support Release;
3 Minute 12 Second Read


Michelle Drolet
10. Don’t trust uniforms. Wearing shirts with company logos on them can be enough to gain access to restricted areas. Verify that visitors really are who they say they are. 9. ID caller from IT. If you receive a call offering IT support for a problem you didn’t know you had, get suspicious. That’s probably
1 Minute 54 Second Read


Michelle Drolet
Towerwall Application Security Alert Vol 13.73 Hackers have amassed a vast collection of stolen data, including 1.2 billion unique username/password pairs, by compromising over 420,000 websites using SQL injection techniques. Researchers monitored the gang for over seven months, thought to be “fewer than a dozen men in their 20s who know one another personally” based in
3 Minute 3 Second Read


Michelle Drolet
1.2 billion logins scooped up by CyberVor hacking crew – what you need to do Hackers have amassed a vast collection of stolen data, including 1.2 billion unique username/password pairs, by compromising over 420,000 websites using SQL injection techniques. Researchers monitored the gang for over seven months, thought to be “fewer than a dozen men in
3 Minute 7 Second Read


Michelle Drolet
Despite all the news about hackers infiltrating major corporations, most businesses continue to leave themselves woefully unprotected. Some surveys estimate more than 70% of businesses perform vulnerability tests on less than 10% of their cloud, mobile and web applications. A majority also confess they have been hacked at least once in the last two years.
3 Minute 42 Second Read


Michelle Drolet
Four major challenges when protecting apps and how to solve them Despite all the news about hackers infiltrating major corporations, most businesses continue to leave themselves woefully unprotected. Some surveys estimate more than 70% of businesses perform vulnerability tests on less than 10% of their cloud, mobile and web applications. A majority also confess they
3 Minute 48 Second Read


Michelle Drolet
When an international law enforcement action earlier this month knocked out theGameover botnet, one happy consequence was the takedown of the servers that the CryptoLocker ransomware needed in order to do its dirty work. Well, any celebration over CryptoLocker’s demise is certainly premature – encrypting ransomware is alive and well. With many victims paying up, ransomware is a
3 Minute 56 Second Read

A new ransomware program, known as Cryptolocker, was identified recently. Ransomware can freeze your computer and ask you to pay a fee, but this malicious ransomware does more than just that. (You can use a anti-virus tool to remove the virus.) Cryptolocker is different from other ransomware due to the fact that it allows your
0 Minute 45 Second Read


Michelle Drolet
GameOver Zeus P2P Malware Original release date: June 02, 2014 Systems Affected Microsoft Windows 95, 98, Me, 2000, XP, Vista, 7, and 8 Microsoft Server 2003, Server 2008, Server 2008 R2, and Server 2012 Overview GameOver Zeus (GOZ), a peer-to-peer (P2P) variant of the Zeus family of bank credential-stealing malware identified in September 2011, [1]


Michelle Drolet
Towerwall teamed up with MassBay Community College on May 29 to present the second annual Information Security Summit at MassBay’s Wellesley Hills campus from 8 a.m. to 1 p.m. Over 250 individuals attended the Summit where they interacted with industry experts and participated in various security panel discussions. After a presentation on the “Anatomy of a


Michelle Drolet
10. Use cash or gift cards The threat of identity theft is reduced dramatically if you don’t use your credit card for all your purchases, so consider using cash or even gift cards to pay your way. 9. PCI compliance is important The payment card industry has a set of security standards for a reason:
1 Minute 43 Second Read


Michelle Drolet
Also named to CRN’s “Women in the Channel” and “The Power 50” BOSTON – May 12, 2014 – Towerwall (www.towerwall.com), an IT security services provider for small to mid-size businesses, today announced it was selected for inclusion in a list of the 20 “Most Promising Enterprise Security Consulting Companies.” The list was compiled by the
2 Minute 6 Second Read


Michelle Drolet
My clients often confuse scanning and penetration testing. Organisations should be conducting both external vulnerability scans and penetration tests. If you are storing or transmitting data on the Internet, particularly sensitive data such as credit card details, then quarterly scanning is required to validate your PCI compliance. You also need to conduct a penetration test
4 Minute 1 Second Read


Michelle Drolet
Please save the date and plan to join us for this timely forum on what you need to know about the latest security issues, threats, and technologies that will help you protect your business! May 29, 2014 8:00AM – 1:00PM MassBay Community College 50 Oakland Street | Wellesley Hills, MA 02481 Early Bird Special: $35


Michelle Drolet
We are honored to be named one of CIOReview’s “20 Most Promising Enterprise Security Consulting Companies”. We believe these companies have achieved significant momentum and will rise above the rest http://www.cioreview.com/magazine/20-Most-Promising-Enterprise-Security-Consulting-Companies–YYXO869519378.html
0 Minute 11 Second Read


Michelle Drolet
Welcome to Issue 2 of the Data Security Review It seems that every time you turn around there is a new data security threat in the news, like Cryptolocker and Heartbleed. Our customers are always asking us how to identify the next “big” threat. Our answer is that you cannot keep up with the hackers,
0 Minute 27 Second Read


Michelle Drolet
The cloud computing revolution is well underway and there are lots of benefits to be realized. According to Awesome Cloud research the industry will be worth more than $150 billion this year, compared to $46 billion just six years ago. Mirroring the general trend for SaaS solutions, cloud-based IT security systems can be an ideal fit for
3 Minute 2 Second Read


Michelle Drolet
Criminals are evolving with their techniques for hacking and breaching corporate assets, so security managers need to as well. Here are some ways companies are going beyond standard pen testing in order to increase awareness By Maria Korolov Security professionals have long been running penetration tests against their firewalls and other security systems to find
6 Minute 27 Second Read


Michelle Drolet
Personal and business relationships rely on trust to function, but blind trust in the digital world is downright dangerous. We’re asked to trust companies all the time. We trust them with personal details and they promise to keep them safe. It’s the same story in the enterprise. One company will entrust another to backup and
2 Minute 8 Second Read


Michelle Drolet
Good Afternoon: The IT infrastructure your organization may use for day-to-day business may be vulnerable because of the Heartbleed vulnerability. Sophos a Towerwall partner has prepared a podcast of the Heartbleed vulnerability, which addresses who is likely affected, workarounds and an offer to help determine if you are vulnerable. http://nakedsecurity.sophos.com/2014/04/10/sscc-142-heartbleed-explained-patches-evaluated-apple-chastised-podcast/ If you think you may
0 Minute 40 Second Read


Michelle Drolet
Cisco Security Notice Cisco WebEx Business Suite HTTP GET Parameters Include Sensitive Information CVE ID: CVE-2014-0708 Release Date: 2014 March 18 19:07 UTC (GMT) Last Updated: 2014 March 19 17:58 UTC (GMT)SummaryA vulnerability in Cisco WebEx Business Suite could allow an unauthenticated, remote attacker to view sensitive information transmitted in GET parameters of URL requests.The vulnerability is due to inclusion of sensitive information in


Michelle Drolet
Thanks for all that joined Towerwall at the From Zero to Data Governance Hero breakfast event! Towerwall and Varonis experts gave first-rate information on the importance of pressing data concerns of 2014. Also, Varonis’ speaker gave a great live demonstration on the Data Governance Suite! It was an event well spent! “Towerwall is always looking


Michelle Drolet
by Paul Ducklin on March 12, 2014 We already wrote about Microsoft’s March 2014 patches, noting that, as usually happens, there was an All-Points Bulletin for Internet Explorer coming up. Microsoft doesn’t call them APBs, of course – they are Cumulative Security Updates, with one bulletin covering all the numerous versions, bitnesses and CPU flavors of Redmond’s IE browser.
1 Minute 51 Second Read


Michelle Drolet
Zeus, also known as Zbot, is a malware family that we have written about many times on Naked Security. We’ve covered it as plain old Zbot. We’ve covered the Citadel variant, which appeared when the original Zbot code was leaked online. We’ve even written about the time it pretended to be a Microsoft fix for CryptoLocker, a completely different


Michelle Drolet
Towerwall and Sophos, partnering to protect data integrity in the cloud. Towerwall is now offering Sophos Cloud Endpoint, a new security option for small and medium sized businesses. Sophos Cloud Endpoint offers an integrated, lightweight agent that protects your business, users and their computers. 24/7, anywhere in the cloud. Sophos Cloud Endpoint gives you endpoint
0 Minute 26 Second Read


Michelle Drolet
For today’s Patch Tuesday, Microsoft released seven bulletins (a surprise after only announcing five last week) and Adobe released one. There are four critical advisories, to me the most important of which is MS14-010 affecting Internet Explorer versions 6 through 10. This patch fixes 24 vulnerabilities, one of which has been publicly disclosed. Considering that
1 Minute 29 Second Read


Michelle Drolet
10. Malware is on the rise The threat of malware on mobile platforms is growing steadily as more and more cyber criminals target mobile devices in increasingly sophisticated ways. 9. Byod is a challenge There are obvious benefits to the BYOD (Bring Your Own Device) trend, but it also creates IT challenges and exposes your
1 Minute 32 Second Read


Michelle Drolet
When the healthcare.gov website was launched on Oct. 1 it didn’t take long for technical issues to hit the headlines. Americans trying to register for health care found the website unusable. There were glitches, extremely long loading times, and serious errors, but most worrying of all for anyone entrusting sensitive data to the system was the lack
4 Minute 12 Second Read


Michelle Drolet
I am excited to announce the launch of our quarterly newsletter, the Data Security Review. Each quarter I will be sharing with you what I am hearing from customers, colleagues and data security experts to keep you aware and protected. As we enter 2014, human risk is on everyone’s mind. Even with the most sophisticated
0 Minute 33 Second Read


Michelle Drolet
Please save the date and plan to join us for this timely forum on what you need to know about the latest security issues, threats, and technologies that will help you protect your business! May 29, 2014 8:00AM – 1:00PM MassBay Community College 50 Oakland Street | Wellesley Hills, MA 02481 Early Bird Special: $35


Michelle Drolet
Patch Tuesday January 2014 – Microsoft, Adobe and Oracle by Chester Wisniewski As expected Microsoft delivered four patches on patch Tuesday covering Windows XP, 2003, 7, 2008 R2, Word and Dynamics. All four patches are rated important, the first time in memory that none of the fixes were critical. The Word fix applies to all


Michelle Drolet
Recent vulnerabilities for which exploits are available compiled by the Qualys Vulnerability Research Team. This is a list of recent vulnerabilities for which exploits are available. System administrators can use this list to help in prioritization of their remediation activities. The Qualys Vulnerability Research Team compiles this information based on various exploit frameworks, exploit databases,
4 Minute 2 Second Read


Michelle Drolet
Implementing security practices in your organization’s employees’ daily work habits, and ensuring the integrity and confidentiality of information security, the goals of the Security Awareness Program are: Put information security and its importance into the forefront of your staff’s minds. Spread information security policy and awareness throughout corporate ranks. Build security awareness into the technical
0 Minute 39 Second Read


Michelle Drolet
10. Be clever Create passwords from easy-to-remember sentences, such as < Patriots Win the Super Bowl>, using the first letter of each word and adding numbers and special characters at the beginning or end. (e.g., <12=PwtSB!>) 9. Create a management system Consider creating one, very strong password and appending it with identifiers, such as <!Kr0y-W3n$TOM>
1 Minute 51 Second Read


Michelle Drolet
3 Keys To Keep Enterprise Clouds Secure Outsourcing has won out over ownership, and the rush to the cloud continues to gather pace. Where security is concerned there are two major trends that threaten to expose your company to unnecessary risk. There’s a lack of planning and due diligence when choosing cloud providers, and there’s
3 Minute 54 Second Read


Michelle Drolet
Well, it was certainly a night to remember and much to celebrate With over 325+ people coming to celebrate the 118th MetroWest Chamber of Commerce Annual Meeting! It was a great night with much money raised for United Way’s Feed a Family and our hero’s – Military Veterans. Watch some of the fun we had:


Michelle Drolet
And it keeps getting worse… A widespread outbreak of a sneaky, file-encrypting piece of ransomware called Cryptolocker has many people talking. One very important question raised by Cryptolocker’s success to date: Should you ever pay a ransom to a cybercriminal? Sophos security expert James Lyne, head of global security research at Sophos, went on cable
0 Minute 48 Second Read


Michelle Drolet
Join us for Sophos’ upcoming event: Today’s Threat Landscape – How to Stay Safe Learn how today’s cybercriminals target your computer, identity and money and get practical advice on how to combat anything that comes your way. Sophos security expert John Shierwill explore how malware threats actually work and what you can do to protect your


Michelle Drolet
Published by Michele Drolet, CEO of Towerwall Proper analysis will flag suspicious behavior and allow the IT department to assess the threat and take action to close it down Cybercriminals are employing more sophisticated techniques all the time and far too many companies and organizations still don’t have the protection they really need to safeguard
3 Minute 38 Second Read


Michelle Drolet
Earlier this week a colleague pointed out an intriguing phishing sample that he had come across. It was interesting not because of any great sophistication or complexity, but rather that it illustrated the reuse of an old social engineering trick. The brand being targeted in the phish campaign is Poste Italiane, a well-known Italian group
1 Minute 30 Second Read


Michelle Drolet
Boston News, Weather, Sports | FOX 25 | MyFoxBoston We are delighted to provide $10,000 to the MassBay Scholarship Foundation so the next generation can become cyber security experts. To learn more about the MassBay Foundation and the Information Security Summit Scholarship, click here.


Michelle Drolet
Cyber-attacks take many forms, from cybercrime, to hacktivism, to cyber warfare, and espionage. We’re all used to hearing about phishing attacks and the threat of malware, but organized cyber-attacks perpetrated by groups with political motivations, and sometimes affiliated with foreign governments, are on the rise, and they could represent a much graver threat. Major concerns
3 Minute 38 Second Read


Michelle Drolet
Cybercriminals are employing more sophisticated techniques all the time and far too many companies and organizations still don’t have the protection they really need to safeguard their systems. The prevalence of targeted attacks and advanced persistent threats (APTs) is disturbing. The risk is that security is breached, typically through manipulation of employees using a technique
3 Minute 36 Second Read


Michelle Drolet
Windows admins will have their hands full with the large number of security updates in this month’s Patch Tuesday. There are fixes for 47 vulnerabilities in 13 bulletins for September’s Patch Tuesday cycle. Four of this month’s bulletins are critical. This year’s total for bulletins is up to 79, a considerable increase from 62 at
2 Minute 12 Second Read


Michelle Drolet
While millions of mobile users are anticipating the launch of the new iPhone (5S and 5C), cybercriminals are already making their move to distribute spam that promise to give away the said devices for free, in the guise of a contest. We saw samples of spammed messages that attempted to spoof an Apple Store email
0 Minute 56 Second Read


Michelle Drolet
10. Malware Is On The Rise The threat of malware on mobile platforms is growing steadily as more cybercriminals target mobile devices in increasingly sophisticated ways. 9. BYOD Is A Challenge There are obvious benefits to the BYOD (Bring Your Own Device) trend, but it also creates IT challenges and exposes your company to new
1 Minute 25 Second Read


Michelle Drolet
Read the EDA’s Report on Malware Infections – Malware Infections on EDA’s Systems Were Overstated and the Disruption of IT Operations Was Unwarranted Click here to read.
0 Minute 8 Second Read


Michelle Drolet
Researchers have spotted the first in-the-wild apps to exploit a critical Android vulnerability allowing attackers to inject malicious code into legitimate programs without invalidating their digital signature. The two apps, distributed on unofficial Android marketplaces in China, help people find doctors and make appointments, according to a blog post published Tuesday by researchers from security
3 Minute 4 Second Read


Michelle Drolet
Great information in SC Magazine’s latest whitepaper report, ‘Four steps to respond and recover from sophisticated security attacks’, it discusses the four proactive steps that you can – and should – take now to help keep your organization safe. Click here to view more details: http://bit.ly/131uu2J As we all know, cyber-attacks are becoming more sophisticated
0 Minute 37 Second Read


Michelle Drolet
The overwhelming advantages of cloud-based file storage are not in dispute. You have an automatic backup of your files, which can be accessed on any device, at any time. Small amounts of storage are generally free, and large swathes of server space are coming down in price all the time. They absolve your business from
3 Minute 31 Second Read


Michelle Drolet
Hi all, there is an e-mail scam doing the rounds. The message is an invite from some random person you won’t know with a link (how original). If you get such a message don’t use the link, check your LinkedIn account as if it’s a legit request it will be there waiting for approval. Even
0 Minute 33 Second Read


Michelle Drolet
Remember last week, Facebook leaked email addresses and phone numbers for 6 million users, but that it was really kind of a modest leak, given that it’s a billion-user service? OK, scratch the “modest” part. The researchers who originally found out that Facebook is actually creating secret dossiers for users are now saying the numbers
4 Minute 35 Second Read


Michelle Drolet
Towerwall is proud to offer our new Alternative Cloud-based File Sharing Solutions Cloud based file synchronization services have exploded. Organizations need to be able to provide a modern collaboration experience with the infrastructure that they’ve already invested in, and that they already know how to manage and protect. Watch the video below for more: To learn
0 Minute 23 Second Read


Michelle Drolet
Wherever an app originates from, it is vital that you can vouch for its security before it is circulated The enterprise has gone mobile and there’s no turning back. And while the BYOD movement has received plenty of attention, IT departments are getting a handle on the security risks of personal mobile devices in the workplace. The
3 Minute 42 Second Read


Michelle Drolet
by Darin Dutcher (Threat Research) Last month, the hacker collective Anonymous announced their intention to launch cyber-attacks against the petroleum industry (under the code name #OpPetrol) that is expected to last up to June 20. Their claimed reason for this attack is primarily due to petroleum being sold with the US dollar instead of currency
4 Minute 3 Second Read


Michelle Drolet
Midsummer Patch Tuesday (or midwinter, depending on your latitude) takes place on Tuesday 11 June 2013. As you probably already know, Microsoft publishes an official Advance Notification each month to give you early warning of what’s coming. These early notifications generally don’t give any details, summarizing only the basics, such as: The number of Bulletins


Michelle Drolet
Check out Search Security’s article – “HIPAA Omnibus Rule, PPACA challenge enterprise compliance management”, where our own Natalie Kmit and the Information Security Summit 2013 are highlighted: HIPAA Omnibus Rule, PPACA challenge enterprise compliance management WELLESLEY, Mass. — For information security professionals, compliance-related tasks have often proved to be a trying yet necessary part of the job.
1 Minute 30 Second Read


Michelle Drolet
Many companies have embraced the BYOD trend. They may even have developed applications that enable employees to have 24/7 access to business data and tools. The benefits can be counted in productivity boosts and flexibility, but there is a real and present danger that is being ignored all too often. How many of these enterprise
3 Minute 37 Second Read


Michelle Drolet
Islamist Element in Attacks. A pro-Islamic, anti-American hacking campaign appears to have jumped the gun and started early with hundreds of sites being compromised today. Set to take place on May 7 this month – thought to be US time – and targeting government sites in the US, Israel and India, the campaign is called
1 Minute 33 Second Read


Michelle Drolet
The BYOD trend shows no sign of abating as more and more organizations recognize the potential benefits in terms of cost and convenience. According to a recent surveyby Good Technology, 76 percent of enterprises are now supporting BYOD and the majority of those that still don’t are planning to do so in the near future. When
3 Minute 31 Second Read


Michelle Drolet
Don’t underestimate the damage that malware proprietors can unleash if the right security policies aren’t in place. Bring-your-own-device (BYOD) programs and cloud computing — two of the biggest enterprise trends from the last couple of years — go hand in hand. Employees want to be given the latitude to use their smartphones for work, and
3 Minute 16 Second Read


Michelle Drolet
Please join us for this timely forum on what you need to know about the latest security issues, threats, and technologies that will help you protect your business! May 30, 2013 8:00AM – 1:00PM MassBay Community College 50 Oakland Street | Wellesley Hills, MA 02481 $45 Pre-registration required. To register visit: http://tinyurl.com/ITsecuritysummit DEFENDING YOUR DATA Content


Michelle Drolet
Top Ten Malicious URLs Top 10 malicious URLs blocked by the Trend Micro™ Smart Protection Network™ infrastructure in 2012 Top Ten Malicious URLs Top 10 malicious URLs blocked by the Trend Micro™ Smart Protection Network™ infrastructure in 2012. Top Ten Spammers Top 10 spam-sending countries in 2012. Rank Country 1 India 2 Saudi Arabia 3
0 Minute 16 Second Read


Michelle Drolet
Network World – The enterprise is increasingly turning to mobile app developers for solutions to leverage interest in BYOD. Gartner estimates that 70% of mobile professionals will conduct their work on personal smart devices by 2018. The app development boom has fostered a competitive environment for developers and there is a focus on speed. But In the rush to deploy enterprise
3 Minute 55 Second Read


Michelle Drolet
As the app revolution has gathered pace and smartphones and tablets have become ubiquitous, the importance of testing app security has grown. Many companies have embraced the BYOD trend. They may even have developed applications that enable employees to have 24/7 access to business data and tools. The benefits can be counted in productivity boosts
3 Minute 48 Second Read


Michelle Drolet
The convenience of mobile devices has led to their rapid proliferation in the work place. But along with that convenience come security and compliance issues contributing to the degeneration of trust. Risk management for mobile devices is of rising concern, particularly in highly regulated industries such as healthcare and finance. In order to detect security
3 Minute 2 Second Read


Michelle Drolet
Security researchers from the Vulnerability Lab have identified a serious security hole that could affect a number of companies which rely on Barracuda products. They’ve discovered a high severity validation filter and exception handling bypass vulnerability in Barracuda’s appliances. According to the experts, the input filter that’s designed to block out persistent input attacks is
1 Minute 35 Second Read


Michelle Drolet
It appears that BYOD, “Bring Your Own Device” to work, is beyond just being a growing trend if not currently a sanctioned practice within the corporate walls. It may seem that bowing to this desire on the parts of employees would have a lot to offer, not the least of which is a reduction in
3 Minute 5 Second Read


Michelle Drolet
Jan 11 (Reuters) – The U.S. Department of Homeland Security urged computer users to disable Oracle Corp’s (ORCL:$34.8625,$-0.0475,-0.14%) Java software, amplifying security experts’ prior warnings to hundreds of millions of consumers and businesses that use it to surf the Web. Hackers have figured out how to exploit Java to install malicious software enabling them to
3 Minute 2 Second Read


Michelle Drolet
As the year draws to a close, it’s time for us to take a step back, absorb the lessons of 2012, and look at what 2013 and beyond will bring for users, the security industry, and even cybercriminals. We know this time of year is incredibly busy and as a trusted advisor, you expect Towerwall
2 Minute 17 Second Read


Michelle Drolet
Bringing mobile devices to work? Not so fast. Like it or not, the line between the workplace and the home is blurring. Work-at-home arrangements are becoming more common and cloud services make it easier to co-ordinate teams online. People are constantly on call, with the ability to check their emails and stay in touch wherever
3 Minute 38 Second Read


Michelle Drolet
Two security firms, the established Rapid7 vulnerability manager and eGestalt, a cloud-based compliance management provider, have signed an OEM deal that will do something for the IT security industry that hasn’t been done before: a combination security and compliance posture management offering called Aegify SPM. The SPM stands for Security Posture Management, and eGestalt of Santa Clara
2 Minute 27 Second Read


Michelle Drolet
Providing early evidence of tampering can shorten investigation times for breaches and audits. The convenience of mobile devices has led to their rapid proliferation in the workplace. But along with that convenience comes security and compliance issues contributing to the degeneration of trust. Risk management for mobile devices is of rising concern, particularly in highly
3 Minute 3 Second Read


Michelle Drolet
Don’t assume those third-party apps you buy are fully secure. Despite the promise of cloud computing, companies are still buying software. And it is more cost effective to buy an application and plug it into your system than it is to develop anew. How many third-party applications has your company bought off the shelf? How
3 Minute 27 Second Read


Michelle Drolet
Towerwall is proud to be named a Trend Micro Platinum Partner . Towerwall has aligned itself with industry-leading security application and policy management solution providers. These strategic relationships enable Towerwall to offer its customers an integrated approach to solving their security and policy management needs by coupling best-of-breed technology with top-notch integration services. To learn more about
0 Minute 19 Second Read


Michelle Drolet
Everyday there is a new threat with seemingly innocent emails being sent out that look close to an official correspondence from a company, from Paypal, ADP and BBB – to name a few. Cybercriminals are mimicking the online payment processor PayPal in a malicious spam campaign that attempts to dupe customers into downloading malware from
1 Minute 3 Second Read


Michelle Drolet
Security is not a list of things you do. Security is a way of thinking, a way of looking at things, a way of dealing with the world that says “I don’t know how they’ll do it, but I know they’re going to try to screw me” and then, rather than dissolving into an existential
7 Minute 15 Second Read


Michelle Drolet
According to the article in Dark Reading, Study: Phishing Messages Elude Filters, Frequently Hit Untrained Users, many people are still being tripped up by phishing emails. The article summarizes the findings of a survey that was conducted at the Black Hat USA security conference held in July 2012. Of the 250 conference attendees that were polled,
5 Minute 51 Second Read


Michelle Drolet
Towerwall is proud to offer our new Bring Your Own Device (BYOD) Policy Services. In recent years, the workplace has become more mobile than ever, and the mobile worker revolution is, in large part, the need for clear Bring Your Own Device (BYOD) policies. The big idea is that through the use of cloud computing-based
0 Minute 38 Second Read


Michelle Drolet
Towerwall is proud to offer our new VOIP Assessment Services. Do you know if your VoIP phones and servers are segmented from the rest of your network? Even if they are, segmentation alone may not protect your voice assets. Towerwall, Inc. has developed an approach that is extremely effective in testing the security of VoIP
1 Minute 24 Second Read


Michelle Drolet
We are proud to announce our Threat Spotlight, sign up for our Twitter feed and get the latest threats and how to protect against them. Threat Spotlights as of October 15, 2012: AutoInf AutoInf is a component used by many malware families, notably Conficker, Sality and AutoRun. AutoInf is used to automatically run associated
2 Minute 38 Second Read


Michelle Drolet
It’s becoming more and more common for workers to store work-related documents on their smartphones, tablet computers and other devices they bring to and from work each day. While this can be convenient–employees can access important documents at home or on the road–it also creates greater security risks for businesses. Employees’ Devices May Not Be
4 Minute 9 Second Read


Michelle Drolet
After the last zero day exploit on Java we reported some weeks ago it appears that a new 0day has been found in Internet Explorer by the same authors that created the Java one. Yesterday, Eric Romang reported the findings of a new exploit code on the same server that the Java 0day was found some
2 Minute 6 Second Read


Michelle Drolet
Beware any emails which claim to come from privacy@microsoft.com – it could be that you’re being targeted in an attack designed to steal your AOL, Gmail, Yahoo or Windows Live password. At first glance, if you don’t look too carefully, the emails entitled “Microsoft Windows Update” may appear harmless enough. But the grammatical errors and
1 Minute 50 Second Read

As the BYOD trend gains momentum, not all employees are comfortable having their personal phones locked down and controlled as tightly as a corporate-issued device. To get around this issue some organizations are turning to separation techniques to securely manage corporate email, apps, and docs on employee devices while keeping personal data out of sight
0 Minute 48 Second Read


Michelle Drolet
It’s becoming more and more common for workers to store work-related documents on their smartphones, tablet computers and other devices they bring to and from work each day. While this can be convenient — employees can access important documents at home or on the road –it also creates greater security risks for businesses. Employees’ devices
4 Minute 8 Second Read


Michelle Drolet
Microsoft has published evidence of an extraordinary conspiracy in which potent botnet malware was apparently installed and hidden on PCs during their manufacture in China. This is a big deal, the team at Towerwall has been aware that this level of threat and exploitation existed, but none the less surprised. Read the rest of the
0 Minute 19 Second Read


Michelle Drolet
In recent years, the work place has become more mobile than ever, and the mobile worker revolution is, in large part, the reason for the rise in Bring Your Own Device (BYOD) policies. The big idea is that through the use of cloud computing-based collaboration platforms, enterprise-class companies can save a great deal of money in IT, security and
3 Minute 56 Second Read


Michelle Drolet
A customizable security training program for your review. We’re giving you all the tools you need to keep your employees out of trouble. Whether you’re starting a program from scratch, or just in need of some refresher materials, we’ve got you covered. Here’s whats included in the Towerwall Security Training Toolkit: Program launch guide Employee
0 Minute 25 Second Read


Michelle Drolet
To cap off a summer of devastating corporate data breaches, hackers yesterday posted online what might be the crown jewel of 2012 data dumps: 1 million identification numbers for Apple iPhones, iPads and iPod Touch’s, all purportedly stolen from the FBI. There may also be an additional 11 million Apple device IDs yet to be
0 Minute 20 Second Read


Michelle Drolet
Michelle Drolet, CEO of Towerwall came in at number 32 for the most powerful women for the Channel Reseller Network (CRN). The following 100 are pulled from those ranks as executives who have proven themselves exceptional during the past year. CRN is proud to highlight their achievements. For more information Visit CRN online
0 Minute 15 Second Read


Michelle Drolet
Whether you choose to embrace it or try to resist it, the BYOD (Bring Your Own Device) trend is set to grow. A study by Cisco Systems found that 78 percent of white-collar workers in the U.S. use a mobile device for work and 41 percent indicated that most smartphones that connect to the company
2 Minute 25 Second Read


Michelle Drolet
In a great article by Ted Samson at InfoWorld, that not even a complex, 16-character password guarantees that your cloud-based data and devices are secure. Here is what Ted had to say: This past weekend, Apple co-founder Steve Wozniak predicted that cloud computing would yield “horrible problems” in coming years. By extraordinary coincidence, Wired reporter
1 Minute 48 Second Read


Michelle Drolet
Cybercriminals have spammed out malware, attached to emails claiming to be related to discounts for offers on Groupon. The emails, which have the poorly spelt subject line of “Groupon discount gifts” (in itself something which should ring alarm bells), pretend to come from Groupon, and claim that one of your friends has found a deal
1 Minute 21 Second Read


Michelle Drolet
For those on our Security Alert and Update list we just emailed an article by Graham Cluley on how a malware attack spread as email from your office’s HP scanner, yes that’s right a scanner! In these high-tech times, scanners and photocopiers aren’t just dumb machines sitting in the corner of the office. They are
1 Minute 43 Second Read


Michelle Drolet
Security firm Symantec released malware signature updates for it antivirus software that caused some Windows XP machines to crash into a Blue Screen Of Death — BSOD. The update was sent out to users of Symantec’s security products over about an eight hour period between July 11th and 12th. “The root cause of the issue,”
1 Minute 24 Second Read


Michelle Drolet
For those on our Security Alert and Update list we just emailed this great article by Graham Cluley on the worst possible passwords you could ever choose. Many of you know this is something we preach to our clients on a regular basis and is part of our comprehensive 4E Program. Too many internet users
3 Minute 15 Second Read


Michelle Drolet
Like it or not, the line between the workplace and the home is blurring. Work-at-home arrangements are becoming more common and cloud services make it easier to coordinate teams online. People are constantly on call, with the ability to check their emails and stay in touch wherever they are. The days of having a personal
3 Minute 33 Second Read


Michelle Drolet
Cybercriminals are attempting to infect the computers of internet users, via a spammed-out email that has a malware-infected file attached. Computer users are being warned to be wary of email messages which suggest they contain nude photographs of girlfriends, or claim that they have been reported to the police, as the attached file (Photo.zip) really
2 Minute 50 Second Read


Michelle Drolet
TrendMicro has uncovered certain Android apps (detected as ANDROIDOS_BOTPANDA.A) containing a malicious library file, which when executed, renders the infected device as a zombie device that connects to specific command and control (C&C) servers. What is also noteworthy about this file is that it hides its routines in the dynamic library, making it difficult to
2 Minute 53 Second Read


Michelle Drolet
Many IT departments have weak patching processes – especially on the client-side. And it’s no wonder – patching is tough. Across all industries and platforms, the Window of Exploit (WOE) – that is, the time lag between announced discovery and the availability of a patch – for web-based vulnerabilities is a whopping 233 days, according
3 Minute 1 Second Read


Michelle Drolet
Web applications – particularly those facilitating collaboration and communication – are a boon to sales, marketing and productivity. Teams work together more effectively, salespeople enjoy better leads and marketing tools and customer service reps can more closely connect with those they serve. All of these gains, though, come at a cost: risk. By their very
3 Minute 17 Second Read


Michelle Drolet
There was a recent article in the Wall Street Journal in which the top cyber cop Shawn Henry, spoke how we are loosing the battle with the hackers. At times the hackers can keep up us all night worrying about our networks, employee actions whether intentional or not, we need to remain vigilant and on
0 Minute 47 Second Read


Michelle Drolet
Join us for an unprecedented security event! Friday, April 13th, 8:00 am – AMC Movie Theatre Framingham, MA Join Towerwall, Trend Micro, Application Security Inc., Sophos, Varonis, Vormetric and WAVE for a brief presentation on data and network security followed by a free breakfast and screening of the world premiere movie: The Three Stooges. Click


Michelle Drolet
Boston Business Journal asked Towerwall for required reading for every entrepreneur. Michelle Drolet recommends “The Power of Nice” by Linda Kaplan Thaler and Robin Koval. Nice companies have lower turnover and higher productivity. Click here to read the article.
0 Minute 11 Second Read


Michelle Drolet
Thanks to the blackout of Wikipedia and the efforts of Google and Facebook, the federal bills known as SOPA (Stop Online Piracy Act) and PIPA (Protect IP Act) have been put on the back burner for revision. The actions last month by the three websites generated millions of protest emails against the controversial legislation. But
2 Minute 33 Second Read


Michelle Drolet
The headline reads, “FBI warns of new malware targeting bank accounts,” but it could just as well say, “More new victims born from opening emails.” From the simple act of opening an email and clicking on an attachment, the victim’s username and password to their bank accounts are stolen by a process called keylogging, where
2 Minute 51 Second Read


Michelle Drolet
On Jan. 5, federal law enforcement seized several automobiles worth about $100,000 in value. They had belonged to the former president of the Massachusetts Bank and Trust Company and were taken as restitution for his defrauding the bank in 1997. It seems that not a day passes by when news of banking-related fraud, money laundering,
3 Minute 39 Second Read

Towerwall & AppSecInc are pleased to offer a free webinar to highlight Database Security Top Threats and Tips. Learn more about the current threat climate and top tips for protecting sensitive information in the database. During this one hour presentation, AppSecInc’s CTO, Josh Shaul will discuss how to: • Defend against the latest cyber espionage
0 Minute 28 Second Read


Michelle Drolet
This Thursday, October 20th I will be a guest presenter at the 5th annual Pioneer Valley Information Security Awareness Conference at Holyoke Community College. A comprehensive slate of topics will be discussed, notable will be trends in cyber crime, protecting business data, the security of social media sites such as Facebook and Twitter, and women